I am having trouble with connection of Withings Wifi Scale to internet. Everything worked fine until I have replaced router with UTM 9. For some reason it stopped working.
My setup is simple. I have only one uplink, everything is on simple NAT, Transparent Web filtering was on.
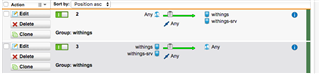
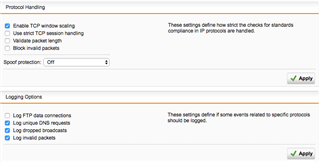
I've tried to disable everything I could, turned off all IPS, ATP, disabled Web Filtering, and just in case added ip of Wifi scale to exception list everywhere, and allow Any - Any rule as top, to rule out everything, and damn thing won't work. Only thing that work is that WiFi scale gets IP from DHCP, get DNS queries, and send equests to Withings server.
Here is the only thing I have noticed in Firewall log:
/var/log/packetfilter.log:2017:03:25-12:37:17 utm ulogd[6952]: id="2000" severity="info" sys="SecureNet" sub="packetfilter" name="Packet logged" action="log" fwrule="0" srcip="192.168.1.85" dstip="89.30.121.150" proto="6" length="44" tos="0x00" prec="0x00" ttl="255" srcport="49154" dstport="443" tcpflags="SYN" info="nf_ct_tcp: invalid packet ignored in state ESTABLISHED "
My understanding is that this packet is logged, and something is wrong with it. So I guess it didn't passed through. Is there way that I can allow him to pass through, just to see what will happen? Maybe Wifi Scale works with those invalid packets :)
fwrule="0" is default rule, and I have no idea how to edit and allow this? My new Any - Any rule is #1, so this one still precedes it.
Any ideas?
This thread was automatically locked due to age.