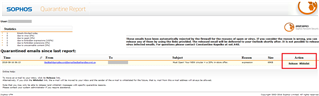
Hello everyone,
We are using UTM version 9.510-5 on hardware appliances.
After updating to version 9.510-5 on Aug 16, 2018, all users started complaining about not being able to release their rejected emails from the quarantine. When clicking on the Release link within Quarantine Report, the browsers (Chrome and Mozilla) display this page:
Bad Request
Your browser sent a request that this server could not understand.
Reason: You're speaking plain HTTP to an SSL-enabled server port.
Instead use the HTTPS scheme to access this URL, please.
Additionally, a 400 Bad Request error was encountered while trying to use an ErrorDocument to handle the request.
The IE11 simply displays a Web page not found (404) message.
I figured out, the Release and Whitelist links within Quarantine Report point to a URL similar to this:
http://firewall:3840/release.plc?proto=pop3&id=233473&secure=39bf55d252ef2ca8e9be4fc5bfa75140
Then, I pasted this link into my browser and changed http to https. It worked just fine, and I got back a normal message from UTM.
Can anybody suggest where in UTM there is a setting to configure the Release and Whitelist links within Quarantine Report sent by email (see image below) to be https instead of http? I seem to have checked everything: Management, Email Protection, and all other sections...
Will appreciate any advice!
This thread was automatically locked due to age.