AT&T Fiber Uverse Gateway Elimination
Those home users fortunate to be in a fiber area have been forced to use the supplied gateway to gain internet access. The gateway does a double nat of sorts, even in the so called passthrough mode. Limitations include 8K (or less) nat table.
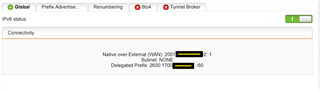
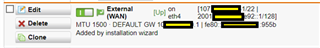
Through a series of convoluted steps, it's now possible to completely eliminate the gateway box allowing UTM to handle the connection directly from the ONT.
In essence, one must obtain the certificates/credentials from a gateway box. The easiest method for the lay person (me) was to obtain a gateway on ebay that hasn't been updated and was still rootable. Other methods include pulling the flash chip and reading in a chipreader and/or other root methods not publicly disclosed. Using another tool the necessary credentials are extracted from this data resulting in several certificate files.
The 802.1x authentication used by the ONT will handled by a third party wpa_supplicant component as this module is not present in the utm OS.
Other functions include starting the wpa_supplicant daemon at startup and a watchdog in case it crashes. Scripts are not the most robost or efficient but are enough to get the job done.
For full details, see this thread on dslreports - www.dslreports.com/.../r31927134-ATT-Fiber-Sophos-UTM-instead-of-gateway. Note the link in the first post referencing a later post (in the same thread). Usual disclaimer; installing third party components is not supported nor recommended, so proceed at your own risk.
This thread was automatically locked due to age.