I tried to expand my network. At the moment it is all wired. I have a ASUS RT-AC87U consumer grade router. It's possible to set it into access point mode. I did so. Furthermore, I gave it a static IP in the range I wanted to use for the WLAN-VLAN. My configuration is as follows:
ASUS RT-AC87U in AP mode, IP static x.x.6.100
The AP is plugged into a VLAN capable switch, into a port which is mapped to VLAN 6.
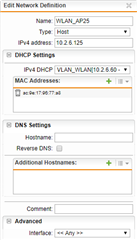
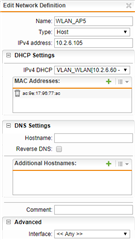
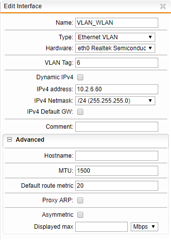
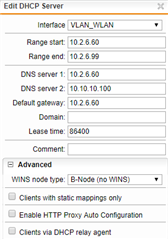
The UTM has a WLAN_VLAN Interface with the same VLAN ID (6). A DHCP Sever (in UTM) is running for this interface with an IP range x.x.6.0 - x.x.6.99. The AP itself has two static entries: x.x.6.100 for the 2.4GHz band and x.x.6.101 for the 5GHz band (it has two distinct MAC adresses).
With this configuration clients won't be able to access the Internet and very often not even the WiFi. They do also not show up in the IPv4 lease table in UTM. The APs management interface isn't reachable under its IP. UTM says "no route to host". To access the GUI I have to set a static IP on my Computer in the x.x.6.x range.
The same is true for the situation, when the ASUS RT-AC87U is in router mode (same configuration as above). But now the router handels DHCP itself, all the clients get connected and have internet connectivity - when I disable SSL scanning. But with this configuration I am not able to let the devices communicate with each other, if they are in different VLANs. (Say a hardwired printer in the printer VLAN and a laptop connected to the WiFi.)
Any idea what went wrong? I basically follows this FAQ: How-To us a wireless router with the UTM.
This thread was automatically locked due to age.