Hi,
I try to setup an 2S2 IPsec VPN between SOPHOS SG210 and CISCO ASA.
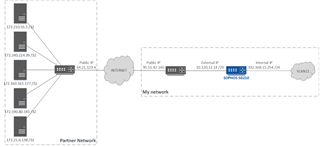
Some details here below (using fictitious IP addresses) :
I need to access to the remote partner servers (172.X.X.X) from local PCs located on my network (vlan11).
The Partner does not take into account our private IP adresses (except 10.120.12.14).
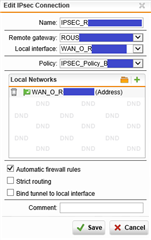
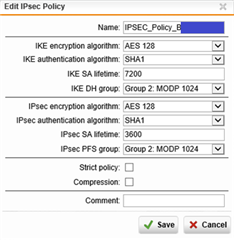
IPSEC Site-to-site VPN configuration (IPsec Policy is weak but requested by the partner):
WAN_O_RXXXX (Address) =10.120.12.14 /29
RG_BVXXXX = 64.21.129.4
RH_BVXXXX = 172.210.55.5 /32, 172.240.224.39 /32 , etc.
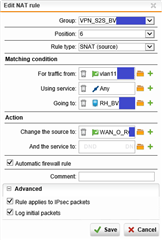
SNAT rules :
I configured 5 rules for each 5 remote hosts (one example here below):
vlan11XXX (Network) = 192.168.11.0 /24
So, here is my problem :
- the tunnel is down until my partner generates traffic from his network. After several minutes, the tunnel goes down (because there is no traffic).
VPN IPSEC LOG until my partner gerate traffic are :
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: received Vendor ID payload [RFC 3947]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ignoring Vendor ID payload [FRAGMENTATION c0000000]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: enabling possible NAT-traversal with method 3
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ignoring Vendor ID payload [Cisco-Unity]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: received Vendor ID payload [XAUTH]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ignoring Vendor ID payload [af0df70b56eff8d779ad8f2f803176a0]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ignoring Vendor ID payload [Cisco VPN 3000 Series]
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: NAT-Traversal: Result using RFC 3947: i am NATed
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: received Vendor ID payload [Dead Peer Detection]
2019:02:13-14:59:37 stan pluto[22808]: | protocol/port in Phase 1 ID Payload is 17/0. accepted with port_floating NAT-T
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: Peer ID is ID_IPV4_ADDR: '64.21.129.4'
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: Dead Peer Detection (RFC 3706) enabled
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ISAKMP SA established
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5166: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#5165}
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5167: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#5165}
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5168: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#5165}
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5169: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#5165}
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5170: initiating Quick Mode PSK+ENCRYPT+TUNNEL+PFS+UP {using isakmp#5165}
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: ignoring informational payload, type NO_PROPOSAL_CHOSEN
2019:02:13-14:59:37 stan pluto[22808]: "S_IPSEC_RXXXXXX" #5165: received Delete SA payload: deleting ISAKMP State #5165
- When tunnel is up, I am able ping all remote hosts (172.210.55.5, etc.) from my network but HTTPS traffic does not pass (however, I configure firewall rules using service any).
Do you have any idea?
Thanks for your help.
This thread was automatically locked due to age.