Hi everyone,
I just purchased a new PC with Windows 10 Pro x64.
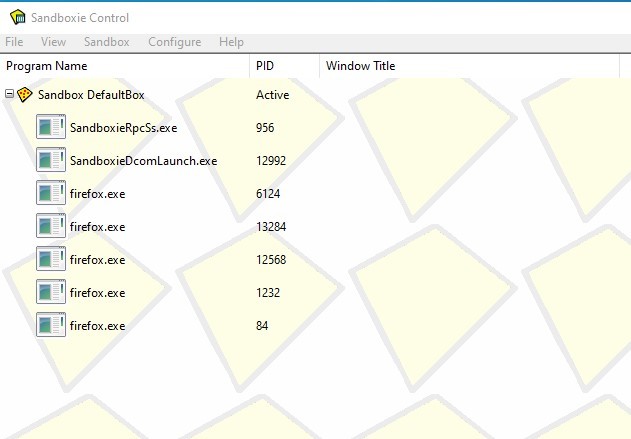
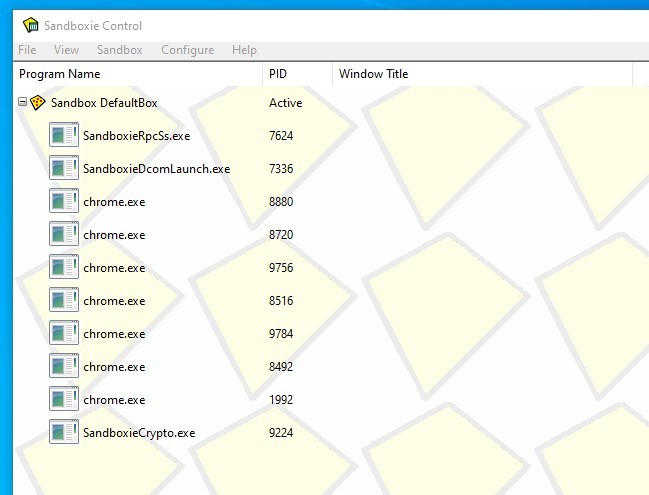
Much to my surprise, I am no longer able to open either Firefox (my default browser) or Chrome in Sandboxie. Nothing is happening when I click on "Run Sandboxed". Or I should say "almost nothing":.. I can see the little red dots on the Sandboxie icon located on the status bar (as it usually does when you are running any sandboxed program), but that's about it! No error message displayed. If I open the Sandboxie Control window, I see a list of the browser processes running (see images below)... but the browser itself never opens!
So, in search of a temporary alternative browser, I tried two other browsers that were still running fine (with Sandboxie) on my old PC (Win7 x64): Brave and Iridium.
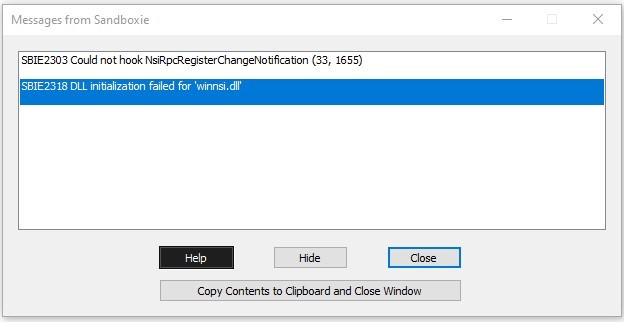
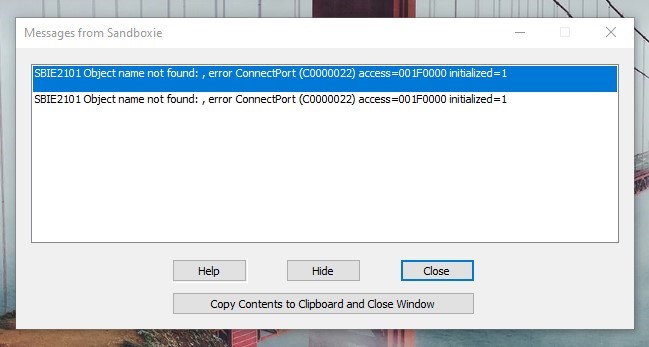
Ironically, Brave and Iridium managed to launch normally on Windows 10 even though they are not officially supported by Sandboxie. However, I get error messages from Sbxie every now and again when starting these browsers. Because they are chromium-based browsers, here are the error messages just in case it would be of any help for resolving the issue with Chrome:
Iridium + Sandboxie:
Brave + Sandboxie:
Please note that all the issues with FF and Chrome described above did not occur on my old PC (Win7 x64), with an exception regarding the issue with Firefox. This issue involving FF had been occurring every now and again over the last few months. However, there was a way to get around it:
- Right-click on the Sandboxie icon (status bar), select DefaultBox and then Terminate Programs.
- Empty DefaultBox.
- Click on the "Sandboxed Browser" shortcut again in order to restart Firefox (which usually restarted "normally" in Sandboxie).
Unfortunately, my "get around method" no longer works in Win10, as I never get Firefox to restart normally (in Sandboxie).
Because of this difference in behavior between my Win7 PC and Win10, I ran the "Troubleshoot compatibility" program on my new PC to test Sandboxie.
Here are the steps I followed:
- Right clicked on "Sandboxed Web Browser" shortcut and selected Troubleshoot compatibility
- "Troubleshoot program" selected
- "I don't see my problem listed" selected
- Windows 7 selected
- Clicked on "Test program"
Results of the test: no change. (i.e. same issues persisted with FF and Chrome while testing in Win7 mode)
Additional info (programs installed, version #, etc.):
- Sandboxie v.5.33.3
- New sandbox with default settings
- Windows 10 x64, v.1909
- Firefox 73.0.1
- Chrome v.80.0.3987.132
- Extension installed on both FF and Chrome: only Webroot Filtering Extension (for now).
- Antivirus software: Webroot SecureAnywhere complete v9.0.27.64, with default settings except for the following: "Warn if any new, untrusted process connects to the Internet" is selected (in Firewall/Webshield). No "warning" or prompt when launching browsers in sandbox. Same antivirus installed on both PCs (Win7 and Win10).
- Windows Firewall
Please let me know if there are any log files hidden somewhere - or any other data - that I could provide to help resolve this issue.
Any help will be much appreciated!