Our bank has requested we setup TLS encryption to secure email transmission with them. I've begun the setup but when I test it against hotmail or gmail I get a failure:
TLS is required, but was not offered by host mx4.hotmail.com
- or -
TLS is required, but was not offered by host alt4.gmail-smtp-in.l.google.com
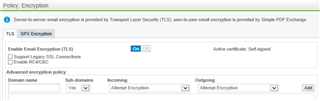
- I've exported our cert from our Exchange and imported it into SEA...
- Both Exchange and SEA are natted to the same IP.
- TLS is enabled.
- Our MX record matches our certificate name
Any assistance would be appreciated or some detailed instructions.
This thread was automatically locked due to age.