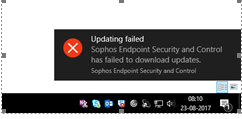
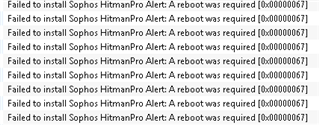
Recently we had vesion update of Exploit Prevention from 3.5 to 3.6.x,
However
1. This has ended up with a pending Reboot Status for all The Systems
2. Sophos in System Tray Shows Broken(Outdated) with an Red Mark - P.S - Panicked Users with Incident Tickets Fired
3. Not all Systems are normal after reboot. Status still same as below
Any one else faced this ?
Manual Re installation is working but cannot consider that for 3k+ Systems
This thread was automatically locked due to age.