Hello.
I have a computer used as a network monitor, which displays a web page console with health statistics on web and SQL servers. Since deploying Sophos, one of the computers is experiencing repeated timeout errors when it tries to load this console. Rebooting the computer will temporarily resolve the problem, but it invariably returns in about 90 minutes. I see this status in Firefox several times while the console is loading.
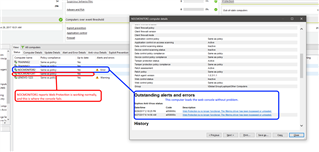
The problem occurs in Chrome as well. With similar hardware, the other computer is not experiencing the problem. The computer where the console works correctly also reports in Sophos Enterprise Console that Web Protection is not working. Here is what the Sophos Enterprise Console shows.
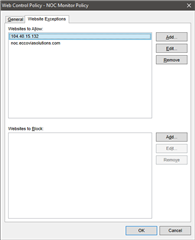
I believe what is happening is Sophos web protection is causing a delay during the loading of the web console, which intermittently causes the browser to time out before the console can completely load. I have created a policy to remove Web Protection from these computers, and that did not seem to help.
How can I configure Sophos to allow this web console to load without problems?
This thread was automatically locked due to age.