New DDE Detection Reports for Sophos NDR
We are excited to announce the activation of two new DDE detection reports for Sophos Network Detection and Response (NDR):
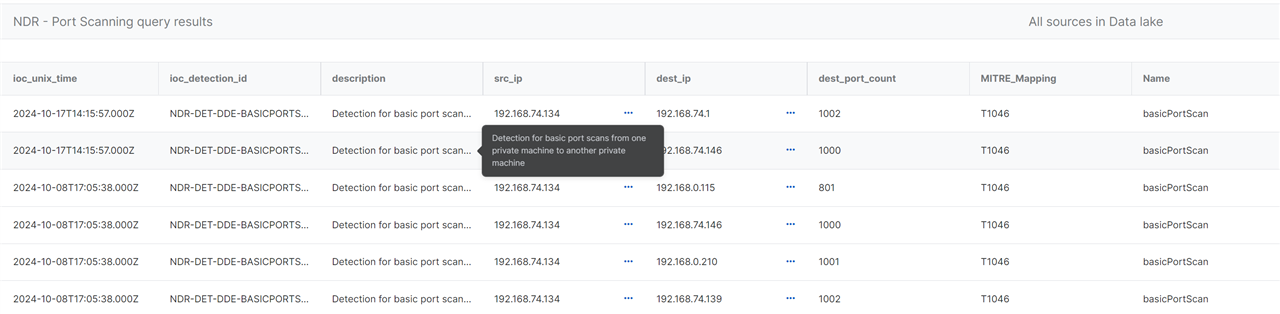
1. NDR-DET-DDE-BASICPORTSCAN
- Overview: This report detects simple port scanning activity, running every hour to identify basic port scans from one private machine to another.
- MITRE ATT&CK Mapping: The report aligns with relevant MITRE ATT&CK tactics and techniques for port scanning detection.
- Detection Logic:
- Identifies patterns of basic port scans through detailed analysis of network traffic between private IPs.
- SQL Query Example
SELECT ioc_unix_time, ioc_detection_id, JSON_EXTRACT_SCALAR(raw,'$.description') description, JSON_EXTRACT_SCALAR(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].src_ip') src_ip, JSON_EXTRACT_SCALAR(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].dest_ip') dest_ip, JSON_EXTRACT(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].dest_port_count') dest_port_count, JSON_EXTRACT_SCALAR(raw,'$.mitre_mapping') MITRE_Mapping, JSON_EXTRACT_SCALAR(raw,'$.name') Name, sensor_id FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_detection_id = 'NDR-DET-DDE-BASICPORTSCAN' ORDER BY ioc_unix_time DESC
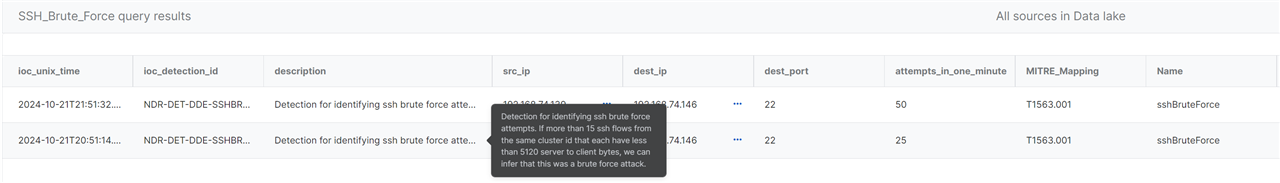
NDR-DET-DDE-SSHBRUTEFORCE
- Overview: This report detects SSH brute force attempts, operating hourly to flag any suspicious behavior.
- Detection Criteria:
- If more than 15 SSH flows from the same cluster ID, with each flow having less than 5,120 server-to-client bytes, the activity is flagged as a potential brute force attack.
- MITRE ATT&CK Mapping: Aligned with MITRE ATT&CK techniques for SSH brute force detection.
- SQL Query Example
SELECT ioc_unix_time, ioc_detection_id, JSON_EXTRACT_SCALAR(raw,'$.description') description, JSON_EXTRACT_SCALAR(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].src_ip') src_ip, JSON_EXTRACT_SCALAR(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].dest_ip') dest_ip, JSON_EXTRACT_SCALAR(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].dest_port') dest_port, JSON_EXTRACT(raw,'$.detection_context[' || CAST(A.x AS VARCHAR)|| '].num_attempts_in_minute') attempts_in_one_minute, JSON_EXTRACT_SCALAR(raw,'$.mitre_mapping') MITRE_Mapping, JSON_EXTRACT_SCALAR(raw,'$.name') Name, sensor_id FROM mdr_ioc_all, UNNEST(SEQUENCE(0,JSON_ARRAY_LENGTH(JSON_EXTRACT(raw,'$.detection_context'))-1)) AS A(x) WHERE ioc_detection_id = 'NDR-DET-DDE-SSHBRUTEFORCE' ORDER BY ioc_unix_time DESC
Additional Details:
- Frequency: Both reports run hourly.
- Severity: Severty for these detection are currently set to 0 (Informational) and will not automatically create an investigation
- Centralized Alerts: Detection findings are automatically sent to the central console for review and response.
- Next Steps: These queries will be added to a future query pack for central to assist in viewing the result data


-

JeroenD
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Comment-

JeroenD
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Children