MITRE Technique T1070.001 - "Indicator Removal on Host: Clear Windows Event Logs" - details adversaries may clear the Windows Event Logs, typically Security, to hide the activity of an intrusion. One should therefore be mindful of tools such as wevtutil and to monitor for Event ID 1102 indicating the Security log was cleared.
I would suggest it would equally be worth considering the deletion of the .evtx file as this conceals the event log entry associated with clearing the log. E.g.
- %Windir%\System32\winevt\Logs\Security.evtx
- %Windir%\System32\winevt\Logs\System.evtx
- %Windir%\System32\winevt\Logs\Application.evtx
As the Windows Event Log service (hosted in a svchost process) has an open handle to these files, they can’t simply be deleted/renamed, however it is possible to delete them at times when the Windows Event Log service is stopped. The EventLog service can be stopped once all dependant services are also not running. For example, running: sc.exe enumdepend eventlog will show only the Wecsvc service is dependant, therefore running the following commands should be sufficient:
sc.exe stop Wecsvc
sc.exe stop EventLog
Where: The Wecsvc service is the "Windows Event Collector" service.
With the Event log service stopped, the .evtx files can be renamed/deleted, when the EventLog service is next started, they will be re-created empty which removes any evidence of the services being stopped using the event log as a source.
Another option that does not require the service(s) to be stopped is to pend the .evtx files for removal for example by the Windows Session Manager (SMSS.exe). This can be achieved at next system boot by setting the PFRO registry value PendingFileRenameOperations or PendingFileRenameOperations1 under the key “HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\”. This registry value, if already exists could be appended to using common registry tools and APIs or simply created in the same way. This technique succeeds as the Event Log service starts after the SMSS.exe process at boot and the time when the Session Manager processes the PFROs.
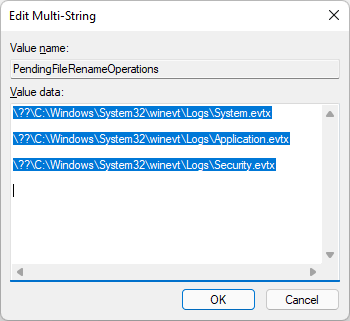
The screenshot shows the PendingFileRenameOperations MULTI_SZ value setup to delete 3 files at next boot.
Note: The empty line following the file denotes deletion, a line immediately following a file would be a rename.
Rather than directly registry tools or registry APIs: The MoveFileEx API, using the MOVEFILE_DELAY_UNTIL_REBOOT flag as used by Sysinternals' MoveFile Tool, is also an option. Examples commands might be as follows:
movefile.exe C:\Windows\System32\winevt\Logs\System.evtx ""
movefile.exe C:\Windows\System32\winevt\Logs\Application.evtx ""
movefile.exe C:\Windows\System32\winevt\Logs\System.evtx ""
The PendingFileRenameOperations registry value will be created or appended to for example:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager]
"PendingFileRenameOperations"=hex(7):5c,00,3f,00.....
Note: As mentioned, this data could also be a value called PendingFileRenameOperations1, both values are processed so it is worth being mindful of both.
Detection indicators may include:
- Stopping the EventLog Service, using the Service Control Manager (SCM) APIs.
- Deleting .evtx files under the %windir%\System32\winevt\Logs\.
- Absence of any event log entry for a short period of time.
- Creating PFROs registry entries (PendingFileRenameOperations or PendingFileRenameOperations1) that reference common system .evtx files.
- Tools such as MoveFile or system tools such as reg/regedit or APIs configured to delete significant system .evtx files. Consider cmdline or MoveFile for paths.
- %windir%\PFRO.log may have reference attempts to removing the .evtx files if there was an issue deleting the files . E.g.
8/14/2021 14:7:38 - PFRO Error: \??\C:\Windows\System32\winevt\Logs\SecurityDoesNotExistForDemo.evtx |delete operation|, 0xc0000034
8/14/2021 14:7:38 - 3 Successful PFRO operations
Happy hunting.
