Hello,
I installed the following VM (VmWare WOrkstation 12) today:
- Windows 10 x64 Pro 1703
- Intercept X Standalone
- Windows Defender disabled
- Firewall Windows active (no additional rules)
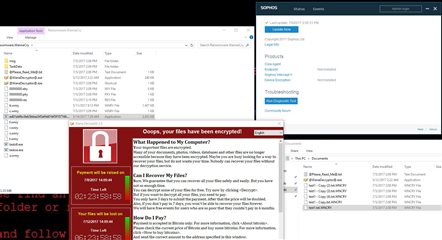
I then created a few textfiles in C:\Users\user\Documents\ and started wannacry. https://www.virustotal.com/en/file/ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa/analysis/1499255455/
The ransomware went trough without any propblem and encrypted the files. Now I wonder if I did something wrong (I hope so!) or if Interceptor is useless at this point.
If more info is needed please let me know.
This thread was automatically locked due to age.