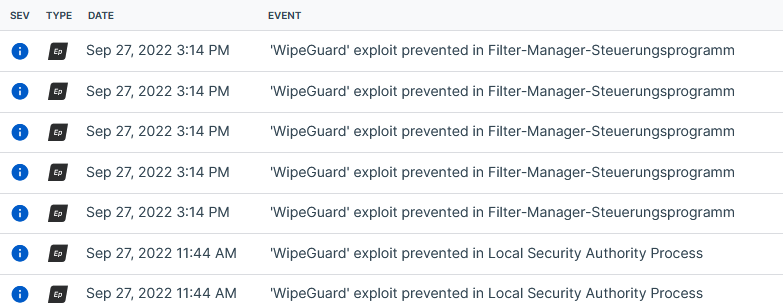
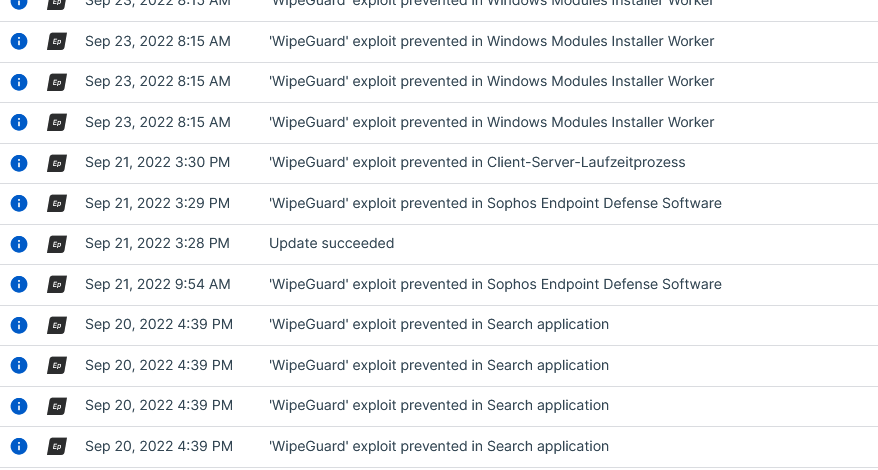
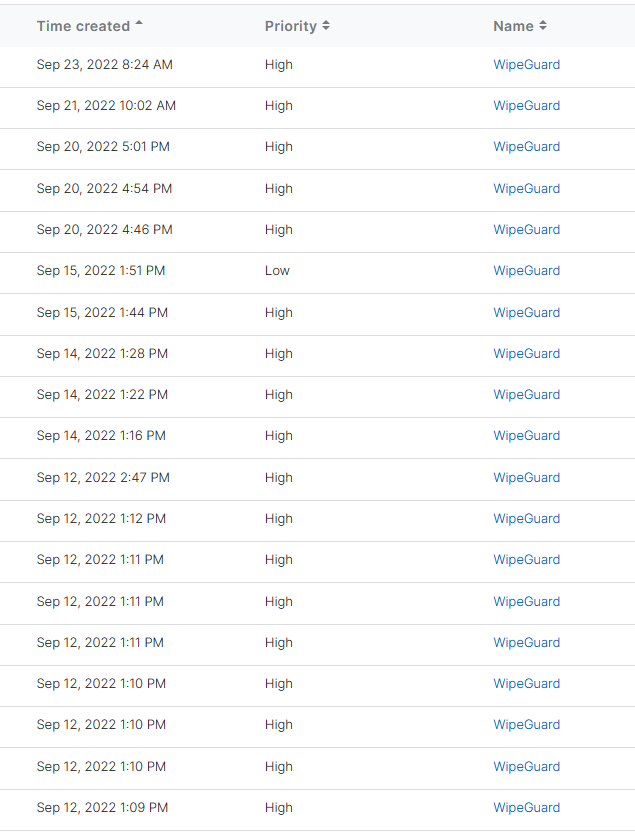
There is one client that does nothing else than reporting WipeGuard preventions.
Even for Sophos Processes. What's the use of that feature and log?
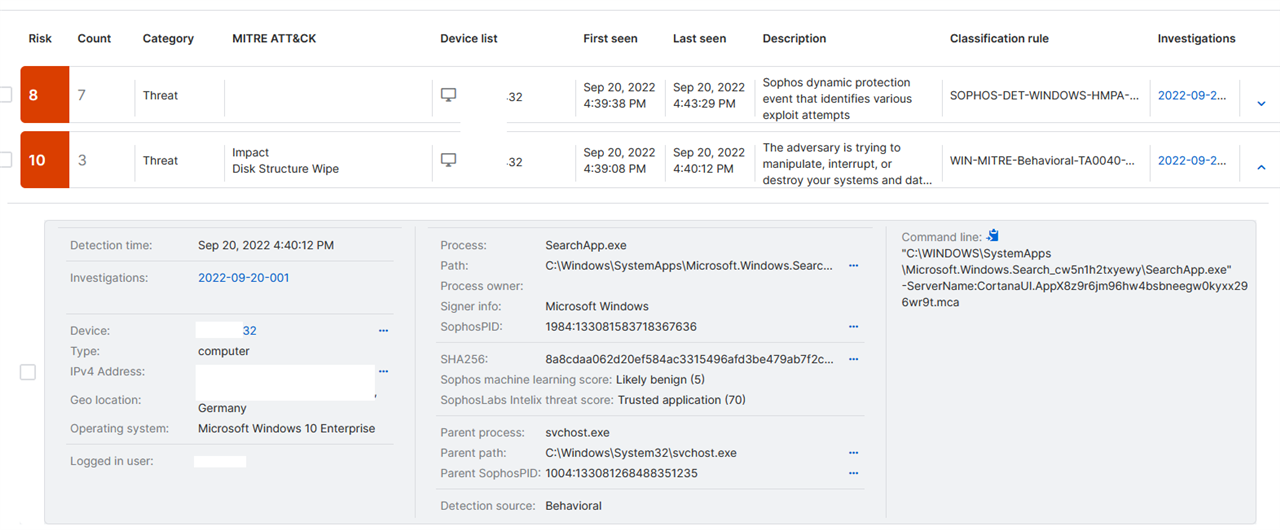
Initial Detection: WIN-MITRE-Behavioral-TA0040-T1561.002

This thread was automatically locked due to age.