Hello
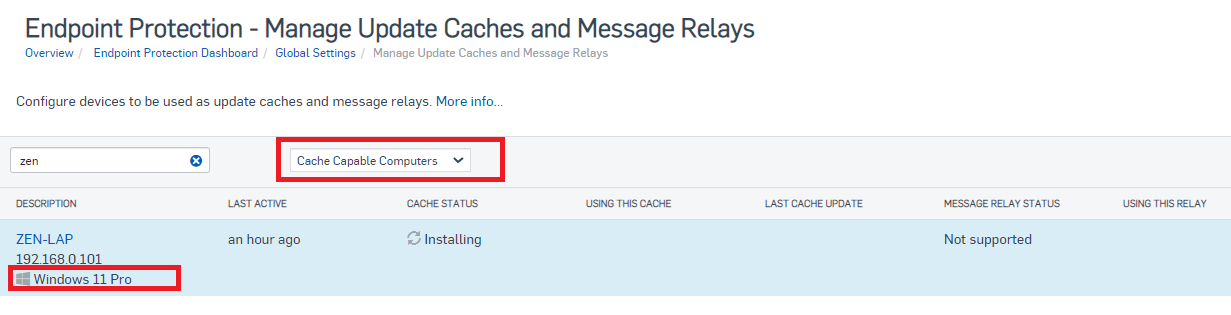
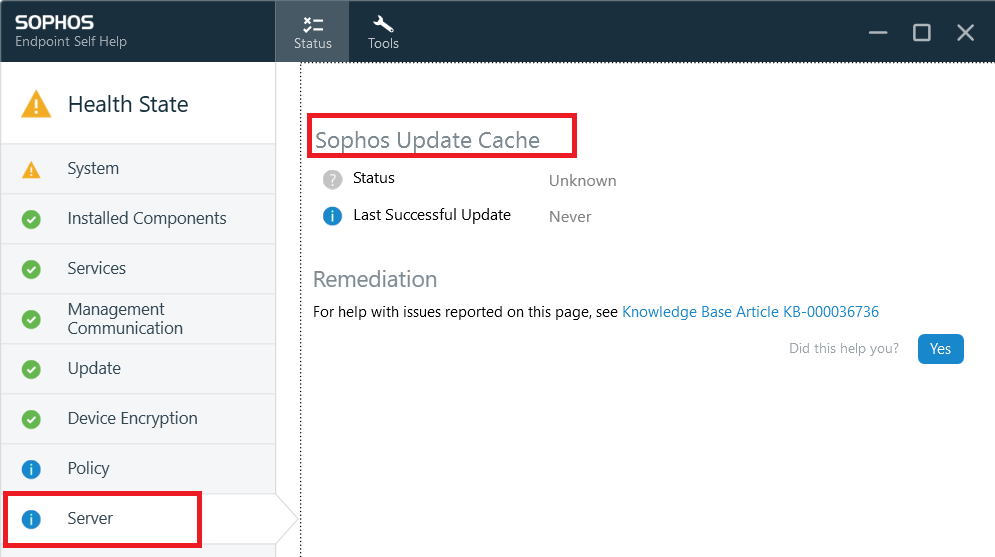
I some instances we use Sophos intercept for servers. and it is quite compicated to manage access for Sophos agent to connect to sophos central.
In Palo Alto Cortex XDR there is such thing as connetion Broker, that can be installed on prem and when installing agent on server/pc you can say that this Cortex agent should use that broker server/service to access updates, reports statuss e.t.c. So i need to open only access to internet for Broker server.
Is there some similar thing in Sophos Intercept ? I was searching for that online but without success, maybe i was just using wrong keywords and that's why I could not find.
This thread was automatically locked due to age.