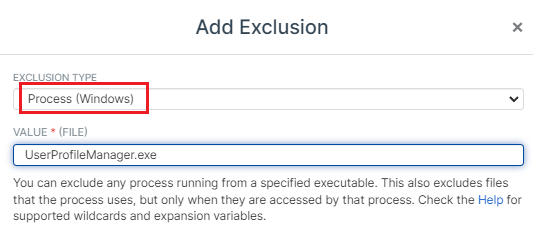
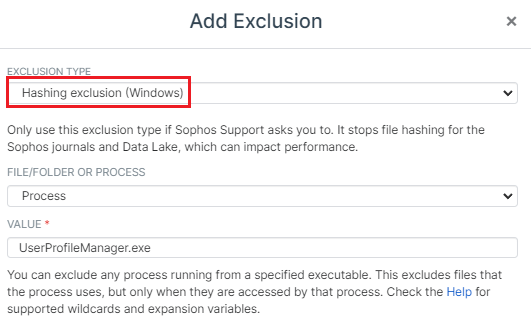
Since we've switched from SEP to Sophos. We've had many random issues with users connecting and receiving various connecting errors. I know that this is a Sophos issue because I removed Sophos from all of our Citrix VDAs and all problems go away. last night I added Sophos back to 2 of our 6 VDAs and all of today's errors are from the 2 that have Sophos installed
I added all of the exclusions recommended by Citrix from the following link, even the one that don't apply to our environment. I made sure that the policy applied to the 2 servers that have Sophos installed.
https://docs.citrix.com/en-us/tech-zone/build/tech-papers/antivirus-best-practices.html
Lastly, we are using UPM (profile management) so I attempted to disable the following scan, but the registry entry does not exist in our environment
https://support.citrix.com/article/CTX238012
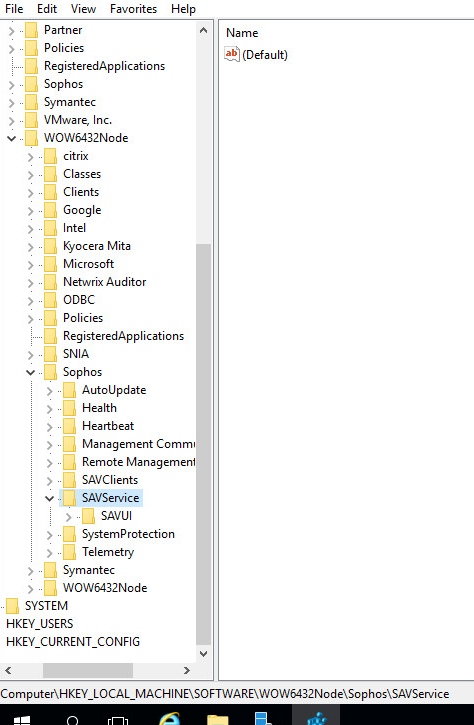
I'm sure I can't be the only person experiencing this issue.
Any assistance would be greatly appreciated.
Matthew Sherman
This thread was automatically locked due to age.