Hi,
seeing this today on several websites.
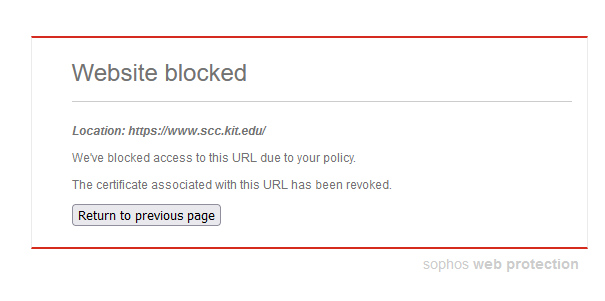
One example: https://www.scc.kit.edu/
- Location: https://www.scc.kit.edu/
- We've blocked access to this URL due to your policy.
- The certificate associated with this URL has been revoked.
We have XG with HTTPS decryption in front of clients and of course, the SSL connection is decrypted by XG.
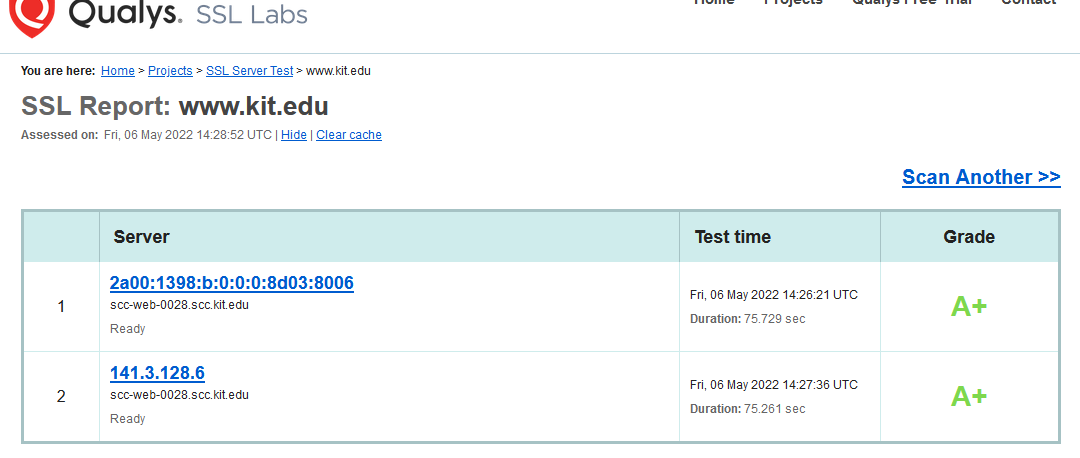
If I skip that website from HTTPS decryption on XG, it's working.
What's the issue with the endpoint?
XG filter active:
2022-05-06T14:22:02.458Z [ 7492: 7732] I [webengine] New connection 0x2bf4e06aa60
2022-05-06T14:22:02.489Z [ 7492:11492] I [check-ip] connection:0x2bf4e06aa60 ip:141.3.128.7 flowId:44865 decision:continue
2022-05-06T14:22:02.519Z [ 7492:11492] I [clienthello] connection:0x2bf4e06aa60 sni:www.scc.kit.edu flowId:44865 decision:decrypt
2022-05-06T14:22:02.548Z [ 7492: 7732] I [revocationcheck] certificate CN=www.scc.kit.edu offline-status:unknown
2022-05-06T14:22:02.548Z [ 7492:11492] I [serverhello] connection:0x2bf4e06aa60 sni:www.scc.kit.edu flowId:44865 decision:allowed
2022-05-06T14:22:02.550Z [ 7492: 7732] I [certgen] cloned certificate <<Certificate Serial=81 86 08 16 a0 1d 12 Subject=CN=www.scc.kit.edu Issuer=C=DE, HERE-IS-OUR-SOPHOS-XG-CERTIFICATE cc NotBefore=2022-05-02 2022 22:03:01Z NotAfter=2022-07-31 2022 22:03:00Z altnames=dph.tm.kit.edu,scc.kit.edu,www.campusgrid.de,www.forschungsgeraeteboerse.de,www.helmholtz-data-center.de,www.orbit.kit.edu,www.rz.uni-karlsruhe.de,www.scc.kit.edu>> as <<Certificate Serial=f4 40 e2 22 69 1c 81 d9 c1 fa b7 35 1e 77 54 70 22 c2 9a 23 Subject=CN=www.scc.kit.edu Issuer=CN=Sophos Endpoint RSA Root, O=Sophos Fingerprint=22 ab 01 01 04 eb 4a 42 94 fb 48 f9 5a ce bb 36 63 3e cd b5 NotBefore=2022-05-02 2022 22:03:01Z NotAfter=2022-07-31 2022 22:03:00Z altnames=dph.tm.kit.edu,scc.kit.edu,www.campusgrid.de,www.forschungsgeraeteboerse.de,www.helmholtz-data-center.de,www.orbit.kit.edu,www.rz.uni-karlsruhe.de,www.scc.kit.edu>>
2022-05-06T14:22:02.551Z [ 7492: 7728] I Revocation duration=0, Subject=CN=www.scc.kit.edu, status=revoked
2022-05-06T14:22:02.554Z [ 7492: 7728] I [revocationcheck] certificate CN=www.scc.kit.edu online-status:revoked
XG filter inactive:
2022-05-06T14:35:58.101Z [ 7492:11492] I [request] connection: 0x2bf4e00e390 url:http://kit.edu/ flowId:46099 decision:allowed riskLevel:2 universalCategory:11
2022-05-06T14:35:58.101Z [ 7492:11492] I page allowed: http://kit.edu/
2022-05-06T14:35:58.105Z [ 7492:11492] I [check-ip] connection:0x2bf4e00e390 ip:141.3.128.6 flowId:46099 decision:continue
2022-05-06T14:35:58.131Z [ 7492:11492] I [scan] connection:0x2bf4e00e390 url:http://kit.edu/ flowId:46099 decision:allowed
2022-05-06T14:35:58.132Z [ 7492: 7724] I [webengine] Closing connection 0x2bf4e00e390 for '': request=345b, response=563b, lifetime=61ms, firstResponse=15ms, businessLogicDelay=0ms, timeInCache=1ms, in=61ms, out=61ms, l.eos=4ms, r.eos=16ms
2022-05-06T14:35:58.139Z [ 7492:11492] I [check-ip] connection:0x2bf4e00e750 ip:141.3.128.6 flowId:46101 decision:continue
2022-05-06T14:35:58.141Z [ 7492:11492] I [clienthello] connection:0x2bf4e00e750 sni:kit.edu flowId:46101 decision:decrypt
2022-05-06T14:35:58.171Z [ 7492:11492] I [serverhello] connection:0x2bf4e00e750 sni:kit.edu flowId:46101 decision:allowed
2022-05-06T14:35:58.191Z [ 7492: 7732] I [revocationcheck] certificate CN=www.kit.edu offline-status:accepted
2022-05-06T14:35:58.197Z [ 7492: 7732] I [certgen] cloned certificate <<Certificate Serial=49 00 ac 1e 26 61 1d 84 f8 1d 6d 7d b8 3f 99 fa 89 03 Subject=CN=www.kit.edu Issuer=C=US, O=Let's Encrypt, CN=R3 Fingerprint=61 26 4f b5 d1 f1 fe aa 02 e2 d8 4b ac 6f 86 59 01 fa 40 7c NotBefore=2022-04-29 2022 22:04:20Z NotAfter=2022-07-28 2022 22:04:19Z altnames=kit.edu,www.cio.kit.edu,www.forschung.kit.edu,www.fzk.de,www.hiu.kit.edu,www.informatikom.de,www.kit.edu,www.kitedu.com,www.nanomikro.kit.edu,www.research.kit.edu,www.th-karlsruhe.de,www.uka.eu,www.uni-karlsruhe.com,www.uni-karlsruhe.de,www.uni-karlsruhe.eu,www.uni-karlsruhe.net,www.uni-karlsruhe.org,www.unikarlsruhe.de,www.universitaet-karlsruhe.de,www.zib.kit.edu,www.zib.uni-karlsruhe.de>> as <<Certificate Serial=a9 f2 48 dd ba 5e f1 e6 a6 2b 3a 91 a4 83 30 63 f6 16 1a 9b Subject=CN=www.kit.edu Issuer=CN=Sophos Endpoint RSA Root, O=Sophos Fingerprint=22 ab 01 01 04 eb 4a 42 94 fb 48 f9 5a ce bb 36 63 3e cd b5 NotBefore=2022-04-29 2022 22:04:20Z NotAfter=2022-07-28 2022 22:04:19Z altnames=kit.edu,www.cio.kit.edu,www.forschung.kit.edu,www.fzk.de,www.hiu.kit.edu,www.informatikom.de,www.kit.edu,www.kitedu.com,www.nanomikro.kit.edu,www.research.kit.edu,www.th-karlsruhe.de,www.uka.eu,www.uni-karlsruhe.com,www.uni-karlsruhe.de,www.uni-karlsruhe.eu,www.uni-karlsruhe.net,www.uni-karlsruhe.org,www.unikarlsruhe.de,www.universitaet-karlsruhe.de,www.zib.kit.edu,www.zib.uni-karlsruhe.de>>
2022-05-06T14:35:58.218Z [ 7492:11492] I [request] connection: 0x2bf4e00e750 url:https://kit.edu/ flowId:46101 decision:allowed riskLevel:2 universalCategory:11
2022-05-06T14:35:58.225Z [ 7492: 7732] I page allowed: https://kit.edu/
This thread was automatically locked due to age.

