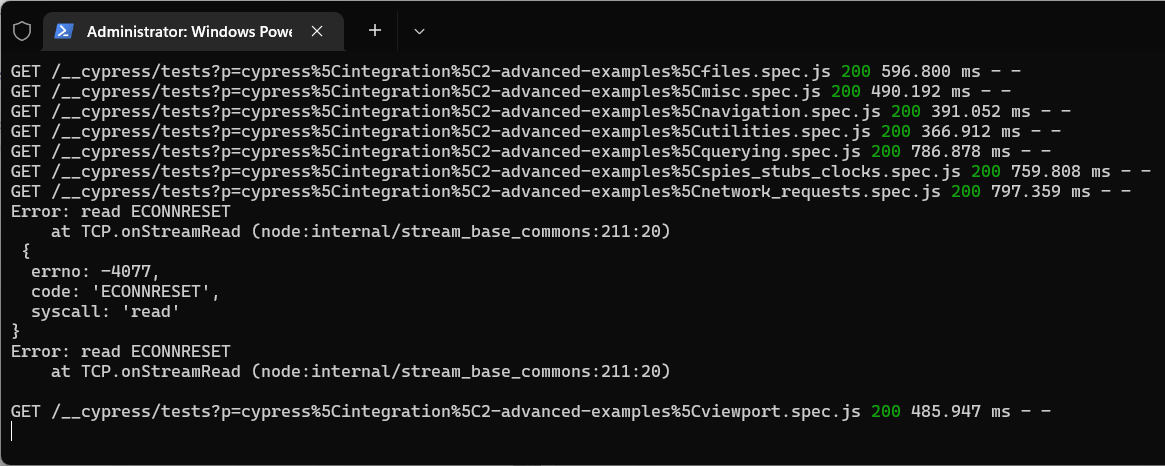
We run Cypress as our web automation tool and as of the past week or two Cypress has been crashing with the error message: Error: read ECONNRESET at TCP.onStreamRead (node:internal/stream_base_commons:211:20)
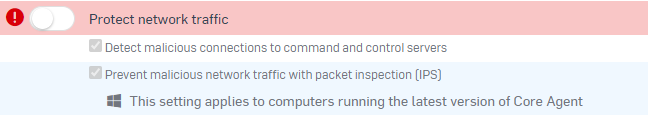
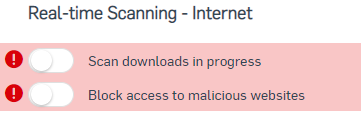
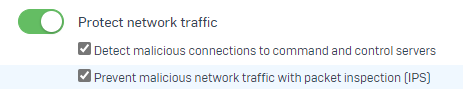
As I'm not in control of the Sophos Endpoint Agent I was able to get the IT team to give me the tamper password to test disabling the 'Network Threat Protection' once this was done Cypress was able to run the automated tests properly.
(Stack Overflow thread with others reporting issue)
Has something changed recently and is there someway that Sophos can fix this so I don't have to disable the network threat protection? If you need any info or help with this let me know.
Thanks
Adrian
This thread was automatically locked due to age.