Hi,
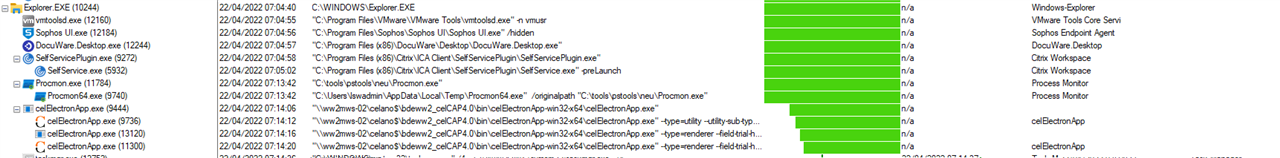
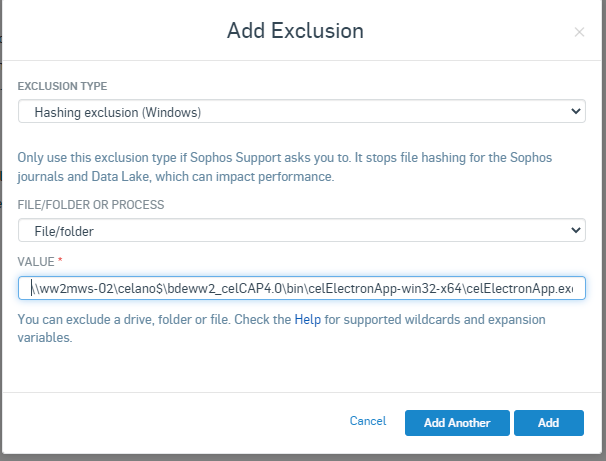
I have a Application with unc path "\\server-01\test$\xyz.exe".
The shortcut of the application is in the same folder with "conf.json" in it.
Sophos Central blocked this program without any events!
Can anybody help ?
best regards,
Thomas
This thread was automatically locked due to age.