Hello,
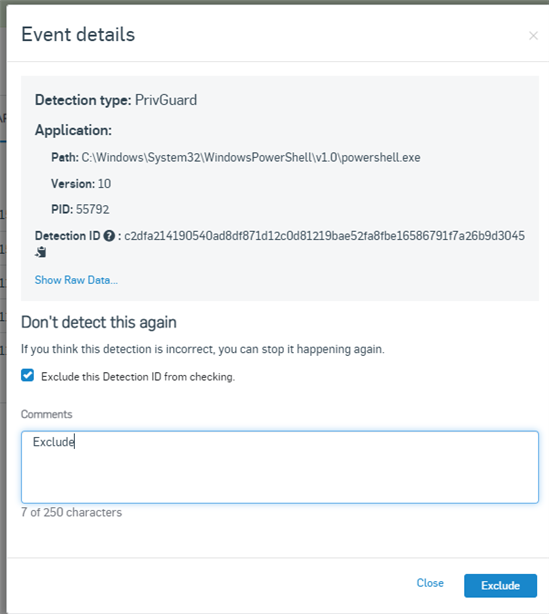
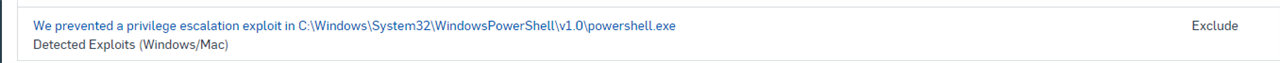
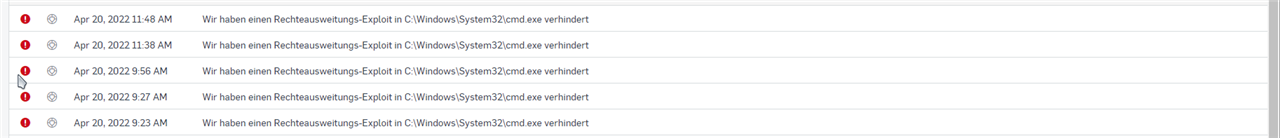
i use gsudo.exe with Windows Terminal to start CMD or Powershell with administrative rights but since i use Sophos Endpoint it shuts down the Terminal app every time the gsudo process opens a new tab.
The Error message is "Malicious Behaviour (PrivGuard) detected.
How can i whitelist the gsudo app?
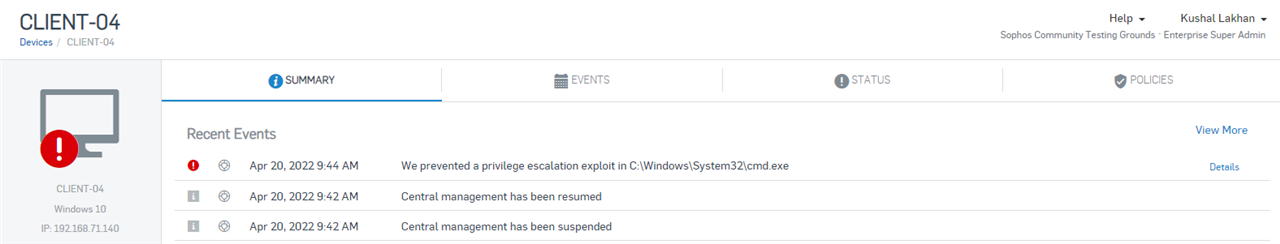
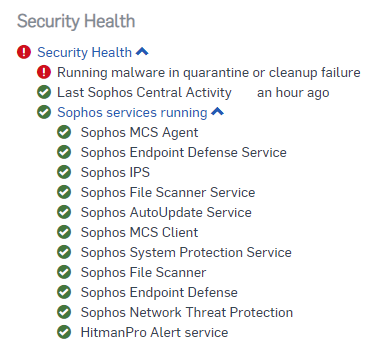
I guess because of this the computer is shown red in the Central console?
This thread was automatically locked due to age.