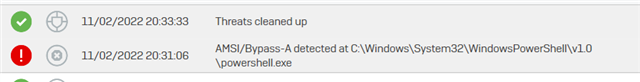
I have two endpoints at two totally unrelated clients where Sophos detected Mal/Polazert-A. Sophos is good at telling me about it, but it doesn't give me any options to remove it. Every time the client reboots their computer, they get a popup from Sophos after login that Sophos found this malware. Now I am concerned it is still running somehow and our client wants to know why we aren't removing malware from their computer.
I explain that Sophos detected and terminated it, but like me, they want to know why it is still there.
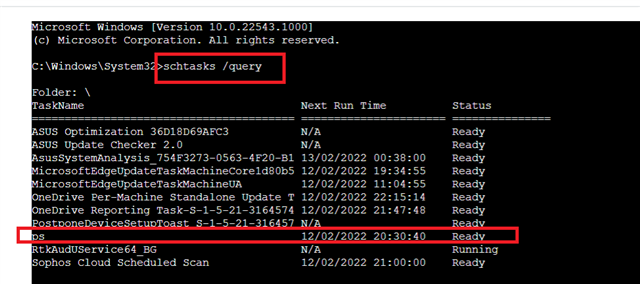
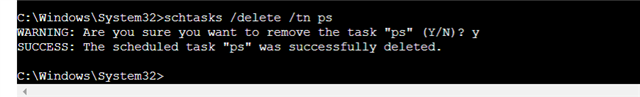
How do I remove it?
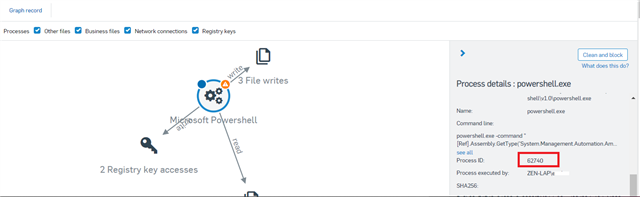
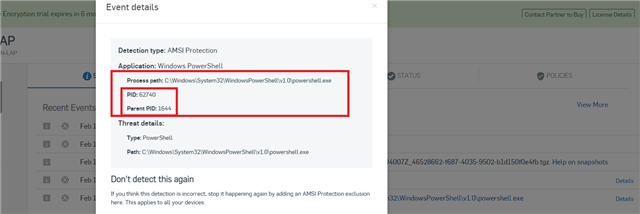
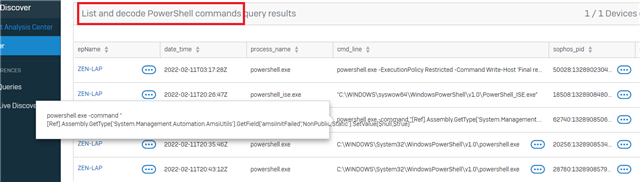
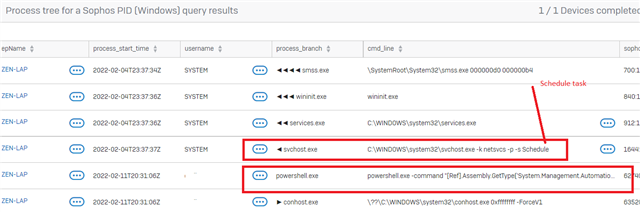
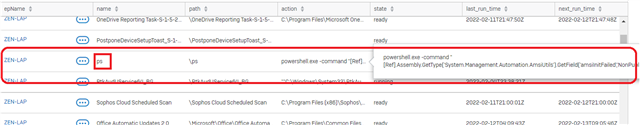
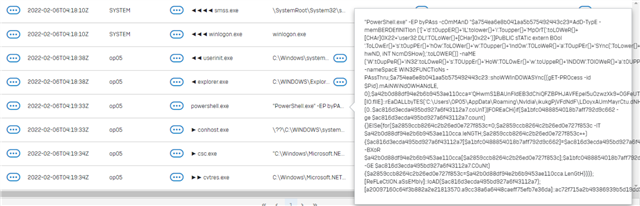
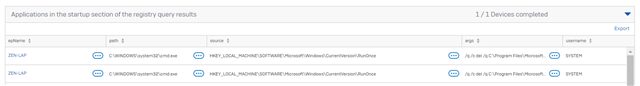
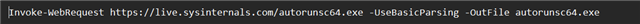
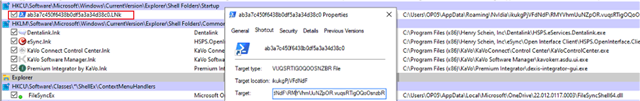
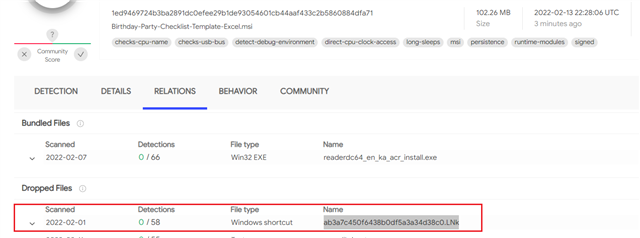
Details of the infection from Sophos Central:
Path:
Name:
Command line:
Process ID:
Process executed by:
SHA256:
Start time:
End time:
Duration:
Actions done to this artifact:
Actions performed by this artifact:
This thread was automatically locked due to age.