Hi community,
I have been running some tests for lateral movement protection, and tried to reach its limitations. I'd like to share my results, and maybe you may have results of different cases that I did not think of.
In order to test, I turned off the Network Threat Protection service from the Windows services.msc app. This turns the status of the endpoint to Red.
Endpoints 1-3 have a Threat Prevention policy which includes self-isolation.
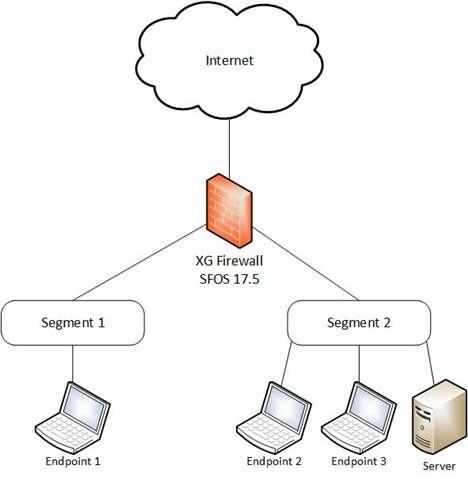
This is the network diagram:
Endpoint 2 was set to have a red status.
All traffic to/from Endpoint 3 was blocked.
UDP/TCP traffic to/from Server was blocked. ICMP traffic was allowed.
All traffic to/from Endpoint 1 was permitted (firewall did not have any restrictions).
UDP/TCP traffic to the Internet was blocked. ICMP traffic was allowed.
What do you think? Are these the results you would have expected?
Cheers,
Steven.
This thread was automatically locked due to age.