We are excited to announce the opening of the Detections and Investigations Early Access Program (EAP). The EAP begins with the introduction of the Detections dashboard which provides a prioritized list of suspicious activity for further investigation. Suspect activities are ranked on a 0-10 risk scale, making it easy for an admin to identify and focus on critical areas. Admins get a description of the suspect activity, how that activity maps to the MITRE ATT&CK framework, as well as details on the time of the event, associated process details, executed command lines, file hashes, device and user details and more, where those details can be provided.
This broad set of information gives the admin vital context to quickly understand if a suspicious item requires action and then easily take the remedial steps.
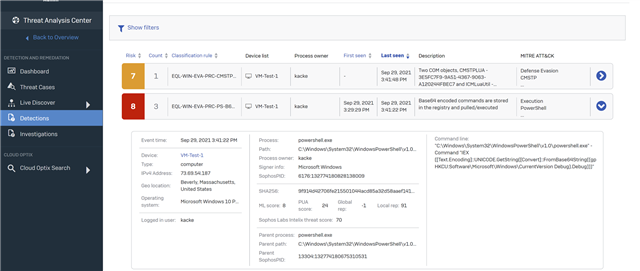
As the EAP progresses further enhancements to the Detections dashboard will be added including enrichments to the available data providing even further context and pivoting which will help admins to dig into the details faster.
In December, we plan to add a new Investigations dashboard which enables admins to collaborate more efficiently and share details on investigations that include multiple, separate detections.
Later in the EAP we also plan to release an Office 365 connector which will enable access to O365/Azure audit logs, giving admins the ability to query this incredibly rich data and incorporate it into their threat hunting and IT operations activities.
Entering the EAP:
Customers need to have an active Intercept X Advanced with XDR/Intercept X Advanced for Server with XDR license or be trialling those products to see and join the Detections and Investigations EAP.
Customers already enrolled in the New Endpoint/Server Protection Feature early access programs can also join the Detections and Investigations EAP.
Joining is simple, from the Sophos Central console click on your username in the top right of the screen, then select ‘Early Access Programs’ and choose the ‘Detections and Investigations’ EAP.
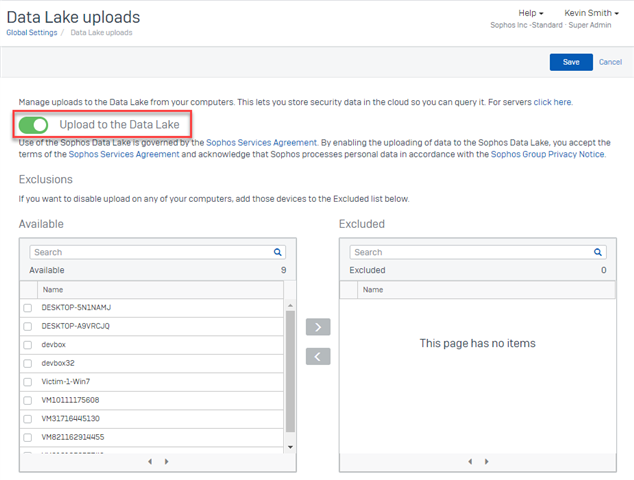
Enable Data Lake Uploads:
Detections are populated based on data observed in the Sophos Data Lake, therefore this functionality requires that you turn on the uploading of data to the Data Lake. In your Sophos Central console select ‘Global Settings’ then under Endpoint or Server Protection (or both) select the ‘Data Lake uploads’ setting and turn on the 'Upload to the Data Lake' toggle. Once enabled we will perform scheduled hydration queries on for your devices which capture interesting threat hunting related data and send it to the Data Lake. From the settings page you can also exclude specific devices from sending data to the Sophos Data Lake if you wish.
Check out the video below for a walkthrough of this new functionality:
Please let us know what you think. You can provide any feedback and suggestions you have to our EAP 'Feedback and Issues' forum in the EAP Community which you can find here.

-

LHerzog
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Comment-

LHerzog
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Children