Hi all,
HTTPS inspection is being enabled by default for devices in the EAP now that the roll out has finished, (both Endpoint and Server).
When users visit websites via browsers the Sophos endpoint will decrypt HTTPS network traffic for the purposes of applying your Threat Protection policy. This decryption allows for deeper and more complete protection, and is recommended for best protection. This inspection technique may, under some circumstances, interfere with successful browsing activity, including for internal websites.
Controls for enabling or disabling HTTPS inspection can be found in Sophos Central under the Global Settings page, in the Endpoint Protection section.
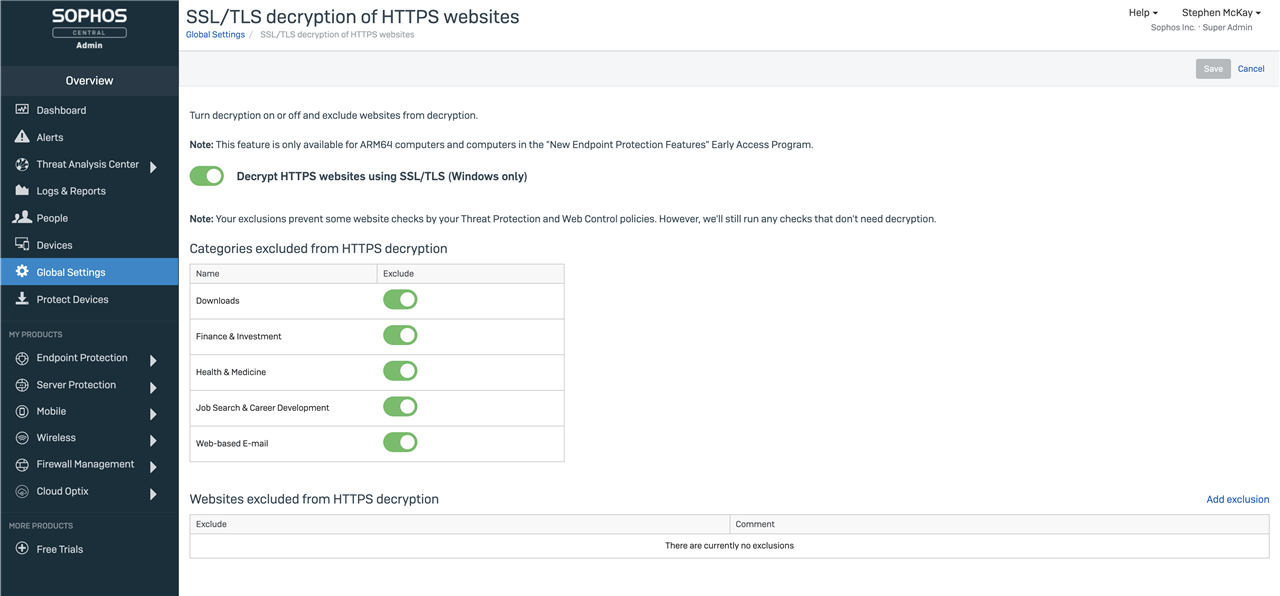
Look for the option “SSL/TLS decryption of HTTPS websites”. This new page offers important controls for managing the HTTPS inspection policy:
- enable or disable HTTPS inspection
- optionally exclude HTTPS inspection for websites in specific categories
- optionally exclude HTTPS inspection for specific websites based on their domain or IP address
There are a few important reasons you may wish to modify those settings:
- websites which rely upon client certificates as part of authentication will not work by default, and will require an exclusion by hostname or IP address
- websites using outdated and insecure encryption algorithms will not be accessible by default, and will require an exclusion by hostname or IP address
- websites using certificates generated by a root Certificate Authority not recognized by Windows may require an exclusion by hostname or IP address
Several additional situations merit mention:
- websites using self-signed certificates will require users to approve access in their browsers, or re-approve access if done previously
- Firefox users may encounter problems unless the option “security.enterprise_roots.enabled” is set in their browser
There will be further updates to enhance the feature over the next few months before we start releasing it to devices outside of the Early Access Program.
Please review the devices you have enrolled in the Early Access Programs and, based on the information above, consider if you need to remove any or make any exclusions via the Settings page.
As always, we welcome your feedback about this enhancements and ask that you provide details of your experience so that we can continue to improve the features and your experience of the product.
Regards,
Stephen

-

Michael Berry
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
-

StephenMcKay
in reply to Michael Berry
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
-

Michael Berry
in reply to StephenMcKay
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
-

StephenMcKay
in reply to Michael Berry
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
-

DarrenTeagles
in reply to Michael Berry
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Comment-

DarrenTeagles
in reply to Michael Berry
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Children