Hi all,
This weekend we are making some policy changes relating to the SSL/TLS decryption of HTTPS websites. We will be adding a toggle for SSL/TLS decryption into the Threat Protection policy for all customers.
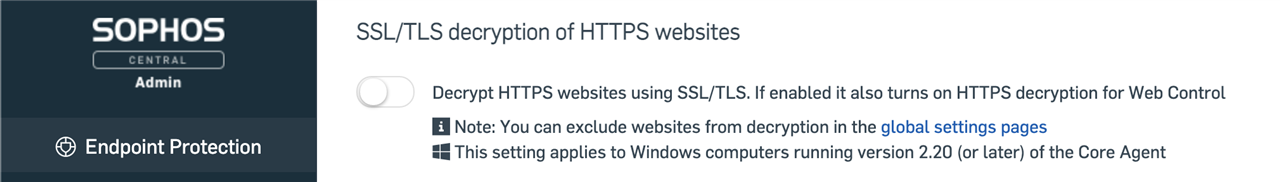
This new setting will determine if Endpoints not in the Early Access Program (EAP) should decrypt HTTPs websites; it will be set to Off by default.
The settings in Global Settings will remain, it serves two purposes;
1. Set exclusions either by website category or by website name
2. Enable / Disable HTTPs decryption for devices enrolled in the EAP, it is enabled by default
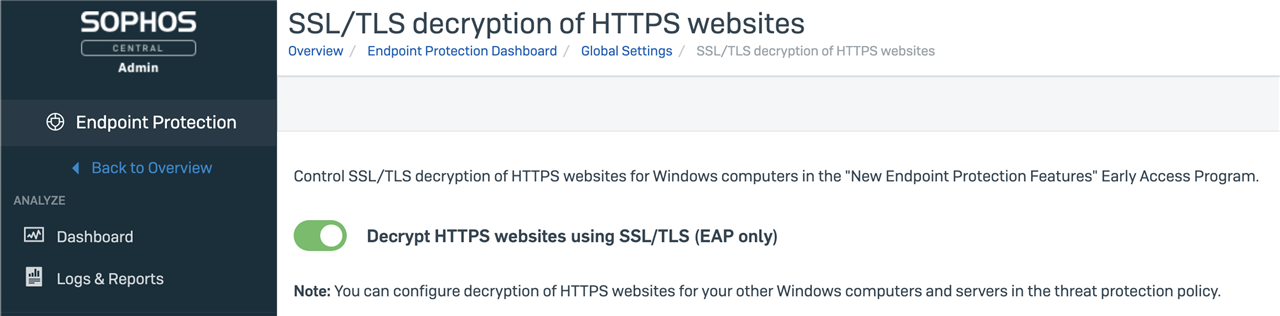
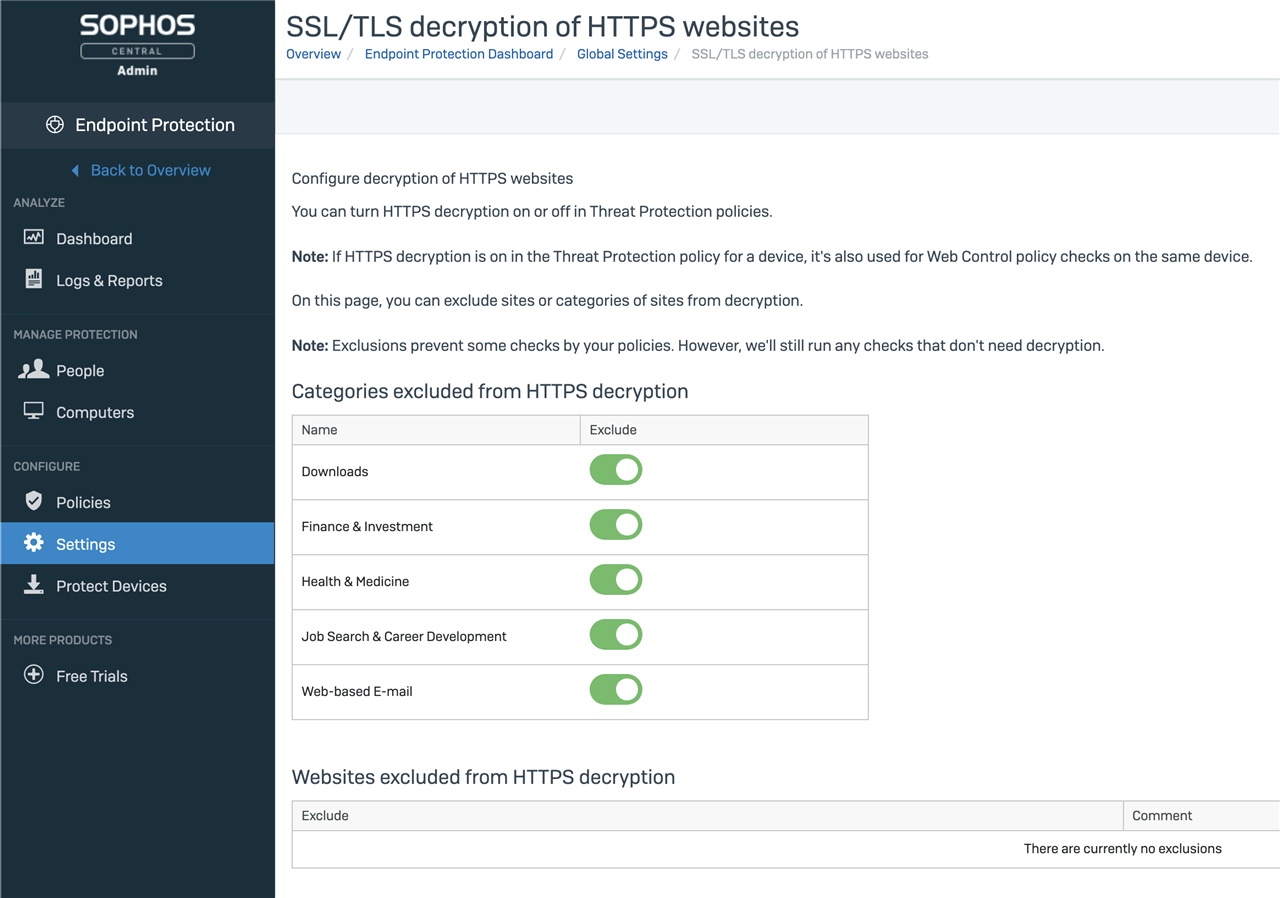
For all customers, the Global Settings page is where categories can be excluded from HTTPs decryption along with individual HTTPs exclusions. Customers not enrolled in the New Endpoint Protection Features EAP will not see the option to enable decryption for their devices
For devices in the EAP, this explains the result of policy settings:
|
HTTPS Decrypt in Threat Protection policy |
HTTPS Decrypt in Global Settings |
HTTPS Decrypt Status on the Endpoint |
|
ON |
ON |
ON |
|
ON |
OFF |
ON |
|
OFF |
ON |
OFF |
|
OFF |
OFF |
OFF |
For devices not enrolled in the EAP, when they have been migrated to the new product architecture (see https://support.sophos.com/support/s/article/KB-000043550 for details), this explains the result of policy settings:
|
HTTPS Decrypt in Threat Protection policy |
HTTPS Decrypt in Global Settings |
HTTPS Decrypt Status on the Endpoint |
|
ON |
ON |
ON |
|
ON |
OFF |
ON |
|
OFF |
ON |
OFF |
|
OFF |
OFF |
OFF |
These changes will be applied if devices are added to or removed from the EAP. If an account is enrolled to the EAP, the changes will only affect devices once they are enrolled into the program.
Regards,
Stephen

-

LHerzog
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
-

bobcook
in reply to LHerzog
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Comment-

bobcook
in reply to LHerzog
-
Cancel
-
Vote Up
0
Vote Down
-
-
More
-
Cancel
Children