



That's right, somehow I'm still employed here at Sophos (at least for now)! I'd like to thank the Web team for letting me know our blog supports GIFs and I'd like to apologize for not following your guidance to "use them sparingly". Let's just say there's a lesson to be learned here... Don't tell Greg about the nice things - he's not allowed the nice things.
Did anyone know October was Cybersecurity Awareness Month across Europe? Nope, neither did I! They should have an awareness month for Cybersecurity Awareness Month and call it Cybersecurity Awareness Month Awareness Month... But wait, wouldn't that need an awareness month for the awareness month awareness...
RuntimeError: maximum recursion depth exceeded
You're probably not here to hear my mind unravel so you best hold on tight as we dive into yet another stream of nerdy consciousness with a side-order of Sophos Central news! LIGHTS! CAMERA! ACTION!
As always, our mindbogglingly talented engineers have been working on a whole range of new features and technologies that are being made Generally Available as well as going into Early Access.
- General Availability
- Early Access Program
(Feel free to click on any of the items above to jump straight to any item in particular.)
General Availability
By General Availability (GA), we mean that this functionality has been released and is ready for you to dive into and start using. Often, new products or features first start out as Early Access Programs (EAP) before they become Generally Available after we've had your insights and feedback, helping us deliver the best possible products.
Intercept X EDR Threat Indicators
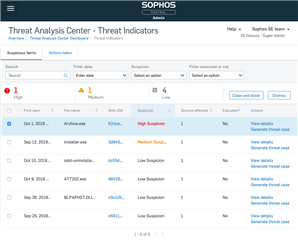
This was such a speedy EAP and GA that my bi-monthly WNIC posts might have to become monthly! Bravo to the teams involved as this has been a huge success and a great addition to Intercept X EDR.
Threat Indicators are an amazing way to investigate what potential, latent threats might exist across your estate. Intercept X will continue to find and block all the bad stuff (that's what it do, bro) but sometimes there are files that land in the grey area between good and bad.
Using machine learning (specifically deep learning / neural networks), our models identify suspicious and potentially dangerous files and present them to you a super-duper, color-coded, prioritized queue. Right from the queue you can clean up the threats, view more details, and even generate a Threat Case to understand how the threat got onto the machine, what it did while it was there, and submit various artefacts to SophosLabs for deeper analysis with all the results visible in the Threat Case itself.
Hop on over to the Sophos Community blog to and check out Kevin from the Product team's video showing-off all the new functionality.
Cloud Optix Update

I'm a huge fanboy of Optix. Many organizations are still scared of "the cloud" (Someone Else's Computer™) especially as oversight over it is so intangible, so untouchable. A server rack downstairs with some VMs on it feels a whole lot easier to get your head around than all those Kubagoober ElasticS3 Compute nodes and so on.
Sophos Cloud Optix helps IT teams around the globe safely harness the cloud and say YES to their colleagues and software developers. Yes to embracing all these amazing, new public cloud technologies without having to fear you'll get pwned and become the next big headline.
This new update continues to expand Cloud Optix's vision into every nook and cranny on all the major public cloud platforms.
The ever so kind Richard, my fellow Product team comrade, has posted a rundown of the HUGE list of new features on the Sophos Community blog. Nice one, Rich!
Device Encryption 2.0
Managing disk encryption is like taking a stroll through a stunning green park filled with kittens and bunny rabbits as the sun shines down from a beautiful blue sky... at least when you're using Sophos Central Device Encryption.
As version 1.0 took the headache out of managing disk encryption, version 2.0 provides some delicious proverbial icing for the metaphorical encryption cake (don't question my analogies).
This new release brings with it some awesome new features:
- Password-protected encrypted files, perfect for sharing an important file with someone over networks and services you're not fully trusting of. No decryption client is needed, all you need is just a web browser! Magic! (It's not magic, it's computer science)
- BitLocker password reset frequency so you can ensure users change their password on a more regular basis than 'never'.
- Even better reporting, making it easier to tell if your drives are encrypted by the OS using software or using the hardware chip inside the drive (some drives have these such as Opal drives).
- Software-based encryption by default as many "self-encrypting" drives (using their own chips inside them to do the encryption) have had vulnerabilities discovered in them that makes their security inferior to just using software-based encryption. We've got your back, as always ;-)
Tom from the Product team posted all about this on the Sophos Community blog so click on over to learn more.
Fgbc orvat n areq naq trg onpx gb jbex!
Email Data Loss Prevention

After yet another successful Early Access Program, our latest Sophos Email DLP functionality is now available for everyone!
Put a stop to emails with data-leaky body content and attachments, inbound and outbound, with our latest enhancements to our existing content control policies.
I wrote about this last WNIC so feel free to give that a read, otherwise jump on over to the Sophos Community blog to hear all about these awesome new features from the ever-radiant Rich from the Product team.
Early Access Programs
EAPs are our way of letting customers get access to upcoming products and features ahead of their release. This month we are launching two new EAPs which customers can join right away and get their hands on our latest innovations before they are released.
Intercept X Enhanced Protection EAP

We're deep into the development of a number of awesome additions to our layers and layers of defense in Sophos Intercept X. Two of these are now in Early Access and we'd love for you to test them out and let us know your feedback.
The first of the new features is our new Anti-Malware Scanning Interface (AMSI) integration. This is a new feature of Microsoft Windows 10 that enables security tech to intercept and analyze scripts like PowerShell and VBScript just before they execute and do their thing, catching the nasty ones before they wreak havoc.
We've been doing this kind of stuff from a behavioral perspective for years now however AMSI makes our lives a little bit easier - PowerShell scripts are provided in their deobfuscated format, meaning we can do more advanced and more performant analysis. Rightfully so, we're very excited to leverage this new Windows feature to make everyone that little bit safer.
The second feature is our new Malicious Network Traffic Protection. This is an on-endpoint packet inspection engine that acts similarly to an Intrusion Prevention System you would find on a network security appliance like our XG Firewall.
What makes our Malicious Network Traffic Protection feature so awesome is that, rather than overloading your endpoints with far too many IPS rules that slows it down to a halt, instead SophosLabs will dynamically push out relevant IPS rules to Intercept X endpoints to provide them with extra layers of protection against the most prevalent threats we are seeing in the labs. This way you get added security without a nasty performance hit and there's no rules that you have to juggle or decide between.
Browse on over to the Sophos Community blog to see how to sign up to the EAP and to access the forums to provide us your feedback.
Email Impersonation Protection EAP

Last by absolutely not least is this rather nifty set of new features coming to Sophos Email.
Some of the most devastating attacks begin with a well-crafted phishing email that impersonates an important person working with or within your organization. To make these kinds of attacks a whole bunch harder, Sophos Email now has a wealth of ways to identify these kinds of attacks.
First, you define a list of your VIPs who are likely to be impersonated - your board members, executive staff, leaders, managers, directors, etc. You can have up to 200 of these so go wild and add plenty! Once you've got the list in place, we'll start employing a whole bunch of techniques to identify any inbound emails that are impersonating your VIPs.
You get a choice what you want us to do to those emails:
- Add a bold banner to the top of the email flagging that it is likely to be an impersonation
- Quarantine the email
- Tag the subject line of the email with some extra text like "Possible Imposter!" or whatever you would prefer
- Delete the email.
It's your call.
The ever-productive Rich from the Product team has gone into much more detail on the Sophos Community blog so head on over and read up on this exciting EAP and get yourself signed up!
Aww shucks, it looks like I've run out of awesome things to tell you about. Save your tears, dry your eyes, for I shall return in two months to celebrate the holidays with you and stuff you brim full of the latest and greatest developments in the world of Sophos Central. Until then, feast upon these fun facts I've found out!
- Male alligators seem to be especially... fond of the tuba, especially when it's playing Bb (B-flat)... One of my local zoos was in this BBC Earth video a few years back that demonstrates the male's fondness for brass instruments.
- Herring fish communicate by using flatulence. No matter how much I claim that I do the same, no-one seems to believe me! Prrrrrp!

-

Funkey
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Comment-

Funkey
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Children