CryptoGuard 5:
A new policy option now sets the default action on detection of ransomware to terminate the process. We have kept the option to only isolate a process should you wish to keep using the setting from CryptoGuard 4.
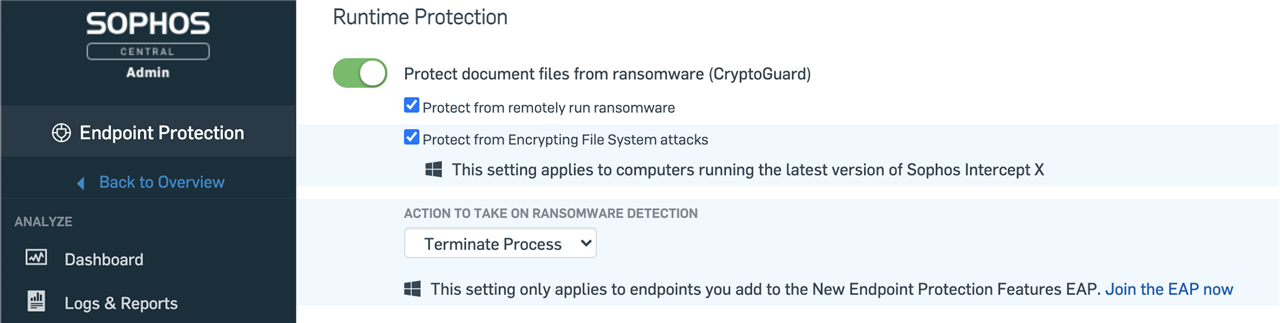
This new release is a design change in how our ransomware detection works; resulting in Sophos detecting more ransomware families and protecting more file types and sizes.
The software release to support CryptoGuard 5 has already released; we will be migrating customers over from CryptoGuard v4 to v5 starting in February. As with all of our feature enablement, it will be done in small batches and you can control the change in action via the Sophos Central policy.
Regards,
Stephen

-

Administrator User569
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Comment-

Administrator User569
-
Cancel
-
Vote Up
0
Vote Down
-
-
Sign in to reply
-
More
-
Cancel
Children