I'm not sure why this is so complicated.
I'm just trying to install Safeguard on windows 10. We have Safeguard Management Center 8.00.2.13 and client version is 8.00.0.251
I had a windows 7 machine with safeguard, I uninstalled safeguard/decrypted the drive first and then upgraded my windows to 10.
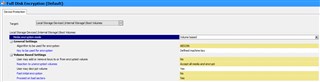
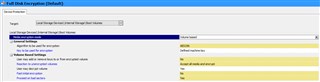
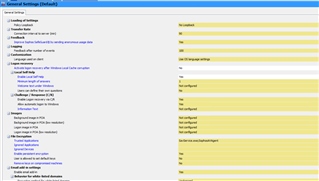
After installing windows 10, I enabled bitlocker first and then installed safeguard.
This is what I have installed.
Sophos Safeguard Client 8.00.0.251
Sophos Safeguard Client Configuration 8.00.0.280
Sophos Safeguard Preinstall 8.00.0.251
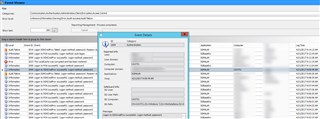
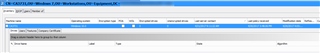
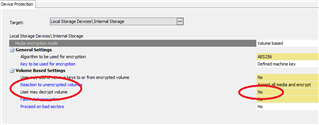
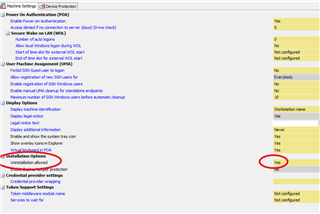
I can sync with the server just fine but the drive is not encrypting. I read somewhere that bitlocker must be enabled in order to install safeguard which is what I did but its still not encrypting the drive. Under the management center, under computer Encrypted drives number read 0.
What steps am I missing?
This thread was automatically locked due to age.