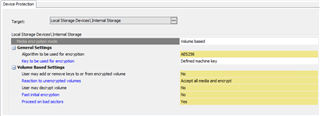
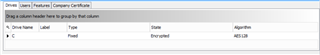
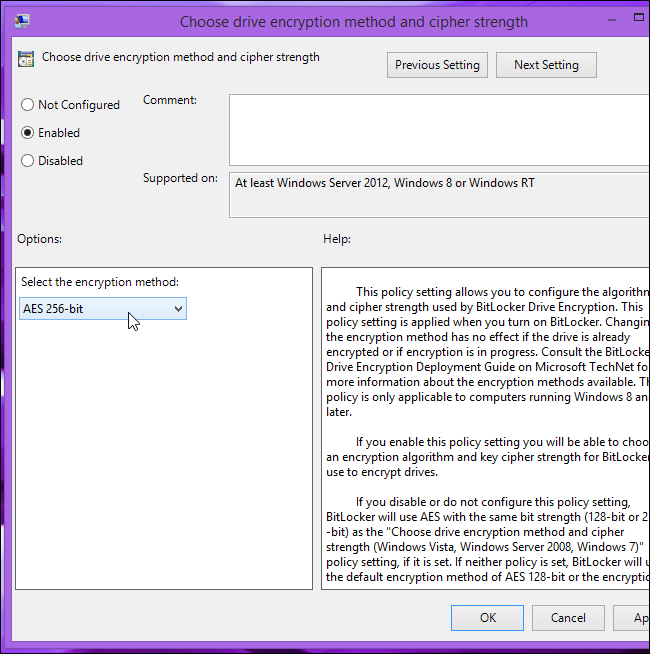
We have created a device protection policy to encrypt volumes using AES256. When the policy is applied to any device, the root volume is encrypted using AES128 algorithm.
This is the policy definition:
This is the final result:
Any idea why?
Thanks in advance.
This thread was automatically locked due to age.