Hi,
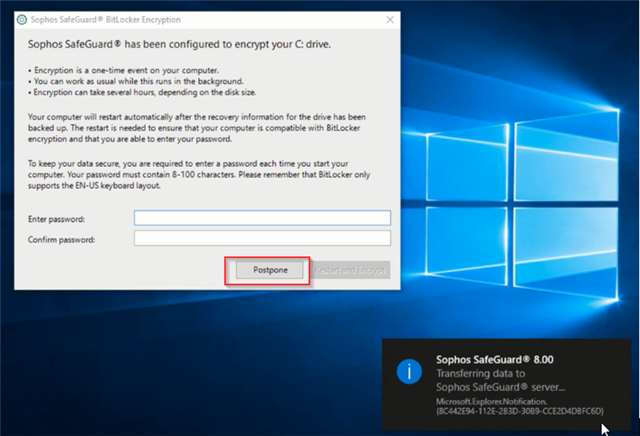
I'm currently deplying SafeGuard client and a bitlocker policy in our company and i have a question regarding the password selection screen.
Standard it shows a postpone option, and about 25% of our users think its funny to keep clicking it, so they never have to choose a password, and thus keep bitlocker disabled.
I was wondering there is a built in option to disable the postpone button, or to keep popping up the windows every hour, to annoy users a bit so they have to set a password for the window to disappear. One notice after every reboot is not sufficient, as many users put their laptop in sleep/hibernate.
This thread was automatically locked due to age.