Hi Michael has helped a lot with my understanding of this but last question or two..
So I was confused and thought POA was the pre boot authentication on Win10 but that's wrong ... When I install safeguard on Win 10 PC's Most of them appear to have TPM.
As a result they are not asking for pre boot pin? I am assuming this is down to TPM.
But i have all the default policiies and in them in my list PIN is the second policy, and it's set to a minimum amount of characters, but that's it... BUT, no device which has TPM seems to be asking the users to add a PIN.
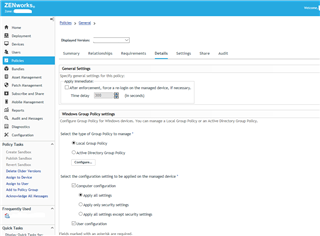
So do I need to create / enable a windows Group Policy to enable it? I've never used AD before this so i'm a bit confused i'm not sure if I need to make a new policy in the sophos console or if I need to go into AD and create a Policy for all win 10 devices saying they need a pre boot PIN?
Where do i force the PC's to use a Pre boot PIN. Which I know should be a series of numbers as it's a PIN not a Number :)
I also realise it doesn't really give much if anything in the way of extra security but our company would like it.
This thread was automatically locked due to age.