Running 8.1
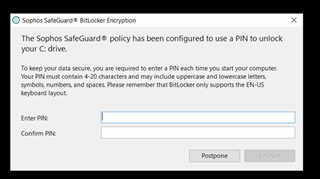
Any ideas My win 10 pc's happily encrypt the HD and also pop up asking for a password for POA.
Win7 64 bit doesn't pop up asking for the POA details. It encrypts the disk fine just doesn't ask for POA or can I only do that on 10?
This thread was automatically locked due to age.