Note: The early access program for ZTNA integration with Sophos Firewall will continue until December 31st, 2023. Please enrol for the early access program to try this integration if you do not have a ZTNA license yet.
Early Access for Sophos ZTNA Gateway on Sophos Firewall is now underway.
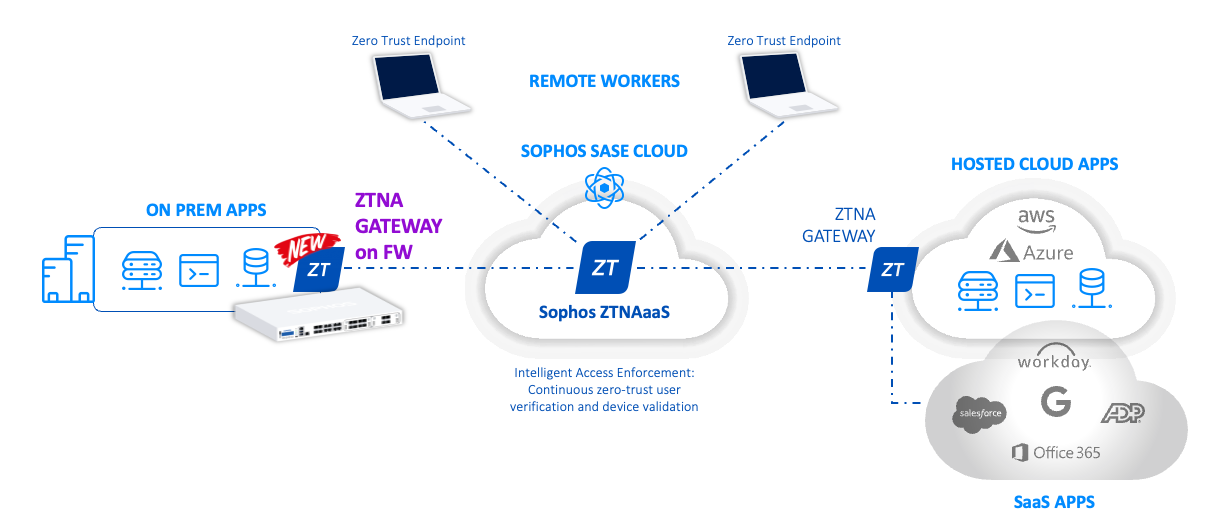
The Sophos Network Security Team is super pleased to announce a new product integration between Sophos ZTNA and Sophos Firewall. With the recent release of SFOS v19.5 MR3 and an update today to Sophos Central, Sophos Firewall customers can now take advantage of the new integrated ZTNA gateway in their Sophos Firewall. This integration makes ZTNA deployments easier than ever by not requiring a separate ZTNA gateway VM to be deployed to provide secure access to applications, systems, and data behind the firewall. Essentially, your Sophos Firewall now also serves double duty as a ZTNA gateway.
There are many benefits to this approach:
- It reduces your hardware footprint and will ensure you do not have to invest in other platform licenses or hardware resources.
- It works everywhere a Sophos Firewall is deployed – head offices, branch offices, public cloud (Azure or AWS)
- Rapid deployment – in just a few minutes
- It works with firewalls in high availability (HA) mode for added resiliency and redundancy.
- It enables easy remote management of your firewall via SSH or the web admin portal without exposing these to the WAN – greatly reducing your surface area of attack.
- It’s free - there is no change in licensing and agent behaviour. Your ZTNA agents will work seamlessly across any of our gateway platforms – now including Sophos Firewalls.
What you will need:
- Join the ZTNA EAP via Sophos Central. The EAPs will now be visible if at least one "Full" license is on Sophos Central.
- Sophos Firewall v19.5 MR3 (recently released)
- Firewall managed via Sophos Central
- Sophos ZTNA term license account or a free trial (MSP Flex licensed customers can use this following GA in October)
- Necessary role-based access control for both Firewalls and ZTNA.
- Please note the redirect URI format change that needs to be added to the identity provider. This new format will apply only to ZTNA gateways deployed on a firewall. The older format will continue for all the other gateway platforms.
Getting Started
Log into your Sophos Central Account to get started. Review the Firewall documentation or jump directly to configuring a cloud gateway and stop by the community forums to discuss the release.
Known Issues/Limitations
| Issue Key | Summary |
| NZT-5626 | ZTNA user portal access is impossible until a resource is created and mapped to a firewall gateway. |
| NZT-5813 | Edit for ZTNA resource type "Web admin portal" fails. The workaround is to delete and create a new resource. |
| NZT-5647 | Resources deployed across firewall gateways connected to different points of presence are not displayed on the user portal. |
| NZT-5621 | Azure AD device compliance check on macOS is not supported via Firewall gateways. |
| NZT-5770 | Delegated admins cannot create firewall gateways. Adequate role-based access control needs to be provided. |
If you’re new to Sophos ZTNA, learn more at Sophos.com/ztna.
