Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
If you have multiple WAN interfaces or public IP addresses and are using MTA mode for email delivery, you must create an outbound rule to forward mail via one interface or IP address.
Depending on your WAN and alias IP configuration, you must do the following:
- If you have a single WAN interface with multiple alias IP addresses. Configure a NAT rule for SMTP with the specific public IP traffic from which traffic will be sent.
- If you have multiple WAN interfaces and no alias IP addresses. Configure an SD-WAN rule for SMTP and the Destination ANY.
- If you have multiple WAN addresses and multiple alias IP addresses. Configure both the NAT and the SD-WAN rules.
- Change the route precedence for all scenarios to Static, VPN, and SD-WAN.
To configure these options, do as follows:
Create a NAT Rule for SMTP with the specific IP traffic will be sent from
- Go to Rules and policies > NAT rules. Select IPv4or IPv6 and then select Add NAT rule.
- The rule is turned on by default.
- Enter the rule details.
|
Name |
Description |
|
Rule name |
Enter a name. |
|
Rule group |
Select a rule group or create one. The firewall rule will belong to this group. If you select Automatic, the firewall rule is added to an existing group based on the first match with rule type and source-destination zones. |
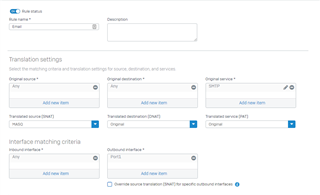
- Specify the translation settings for source, destination, services, and interfaces to match traffic.
|
Name |
Description |
|
Original source |
Specify ANY. |
|
Translated source (SNAT) |
Specify MASQ. |
|
Original destination |
Specify ANY. |
|
Translated destination (DNAT) |
Select Original. |
|
Original service |
Select SMTP. |
|
Translated service (PAT) |
Select Original. |
|
Inbound interface |
Select Any. |
|
Outbound interface |
Select the WAN interface or alias IP address from which traffic specified in this rule exits Sophos Firewall. |
- Optional Select Create loopback rule to allow internal hosts to access other internal hosts, for example, servers.
- Optional Select Create a reflexive rule to create a mirror rule that reverses the matching criteria of the rule from which it’s created.
Note: You can create loopback and reflexive rules for destination NAT rules. They’re created using the original NAT rule ID and name. Changing the original NAT rule settings later doesn’t change loopback and reflexive rule settings.
- Click Save.
The following screenshot shows an example of the NAT rule.
Create an SD-WAN Rule with Destination ANY and Service SMTP
-
- Go to Routing > SD-WAN policy routing. Scroll down to IPv4 or IPv6 SD-WAN policy route and select Add.
- Enter a name.
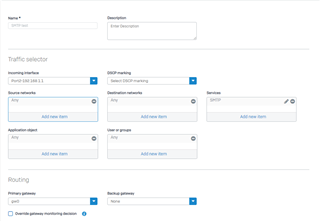
- Select the traffic selector settings.
|
Name |
Description |
|
Incoming interface |
Select ANY. Deleting the interface also deletes the policy route. |
|
DSCP marking |
Select the level of DSCP marking to match incoming packets for priority. For details, see DSCP Value. Expedited forwarding (EF): Priority queuing that ensures low delay and packet loss. Suitable for real-time services. Assured forwarding (AF): Assured delivery, but with packet drop if congestion occurs. Assign packets a higher priority than best-effort. Class selector (CS): Backward compatibility with network devices that use IP precedence in the type of service. |
|
Source networks |
Select ANY. |
|
Destination networks |
Select "Internet IPv4 group" |
|
Services |
Select SMTP. |
|
Application object |
Leave blank. |
|
Users or groups |
Select ANY. |
- Specify the routing settings.
|
Name |
Description |
|
Primary gateway |
Select the primary gateway to route traffic. If you delete the selected gateway, Sophos Firewall will delete the policy route and implement the WAN link load balance to route traffic. Sophos Firewall routes traffic through the backup gateway if the primary gateway goes down. When the primary gateway comes back up, Sophos Firewall routes traffic through it. |
|
Backup gateway |
If you've configured more than one gateway, select the backup gateway. If you delete the selected gateway, Sophos Firewall sets the backup gateway to None. |
|
Override gateway monitoring decision. |
Select if you want to route traffic through the selected gateway, even if the gateway is down. |
- Click Save.
The following screenshot shows an example SD-WAN policy route.
- Sign in to the Sophos Firewall command line console as admin.
- Select option 4. Device Console.
- Type the following command:
- set routing sd-wan-policy-route system-generate-traffic enable
Change the Route Precedence to Static - VPN - SD-WAN
- Sign in to the Sophos Firewall command line console as admin.
- Select option 4. Device Console.
- Type the following command and press enter: system route_precedence set static vpn sdwan_policyroute
- Confirm the change using the following command: system route_precedence show
Grammar
[edited by: Raphael Alganes at 9:46 AM (GMT -8) on 14 Nov 2024]