HI to all,
i have this situation:
LAN 1:192.168.100.0/24
LAN 2: 192.168.200.0/24
LAN 3: 192.168.234.0/24
SSL VPN pool: 192.168.90.0/24
IPsec site-site: local subnet 192.168.234.0 remote subnet 10.11.10.0/24
ipsec tunnel works fine, hosts in subnet 192.168.234.0 manage to reach remote site 10.11.10.0.
Now a request has been made to me, also the hosts in the other LAN networks and in the SSL pool must be able to communicate with the remote site, the problem is that on the other side (remote site) no changes can be made, so I cannot simply include the other subnets in the ipsec tunnel. I think the only way is to do NAT.
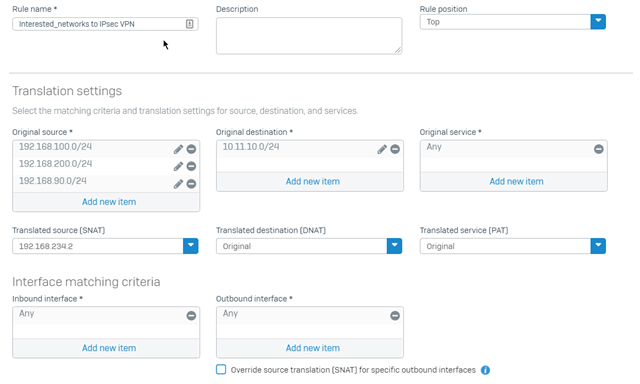
Directly from the ipsec configuration I can flag the NAT option and add another network and it works, the problem is that I can only put one network, and it does not accept a network group.
So I thought about doing a NAT source from NAT roules, but that doesn't work.
The source NAT I configured it like this:
Origianl source: I put in all the LAN networks and SSL pools that interested me
Original destination: 10.11.10.0/24 (remote subnet)
Original Service: ANY
Transalted source: MASQ
Translated destination: original
Translated serice: original
Inbound interface: ANY
Outbound interface: 192.168.234.2(LAN port included in IPsec tunnel)
what am I doing wrong?
Edited TAGs
[edited by: emmosophos at 5:28 PM (GMT -7) on 2 Jun 2021]