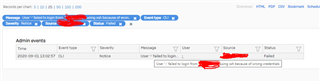
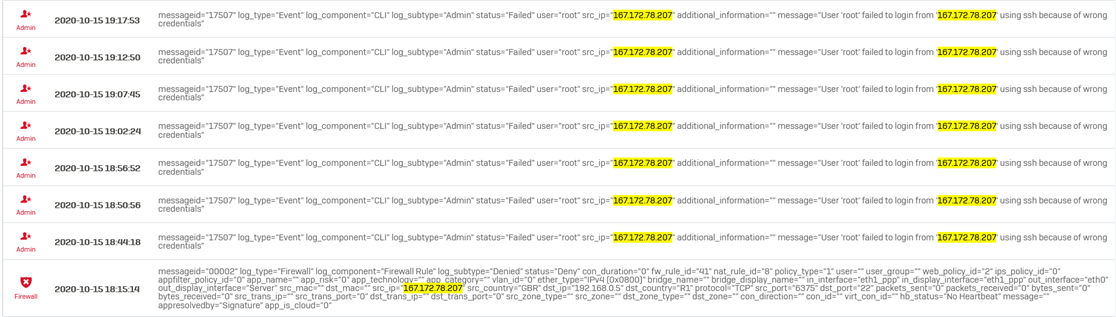
I have received these constant alerts of attempt to access my internal web server, I believe it is a brutal attack attempt via CLI with SSH, but I cannot identify what may be creating this problem, I have already scanned the server itself and I did not find anything that could be suspicious, I also checked the access through the XG wan, ssh is disabled, I scanned ports also open at the server level and I did not find port 22 in the list of open ports. please could someone help me to understand what may be happening?
This thread was automatically locked due to age.