Release Post: Sophos Firewall v21 Early Access Announcement
Whats New Link: https://assets.sophos.com/X24WTUEQ/at/7t8k46h9ttmxt6pn8g58k7wb/sophos-firewall-key-new-features-v21.pdf
General V21.0 EAP1 Discussion Channel: Sophos Firewall: v21.0 EAP1: Feedback and experiences (EAP Thread)
Feel free to share your experience with 3rd Party Threat Feeds and discuss the reasoning, it worked / not worked of importing them.
Active Threat Response with 3rd Party Threat Feeds:
- Active Threat Response has been extended with support for third-party threat feeds to enable easier integration with 3rd party SoC providers, MSPs, industry specific security consortium
- Now, you can easily add additional vertical or custom threat feeds to the firewall which will monitor and respond in the same automatic way – blocking any activity associated with them – across all security engines and without requiring any additional firewall rules
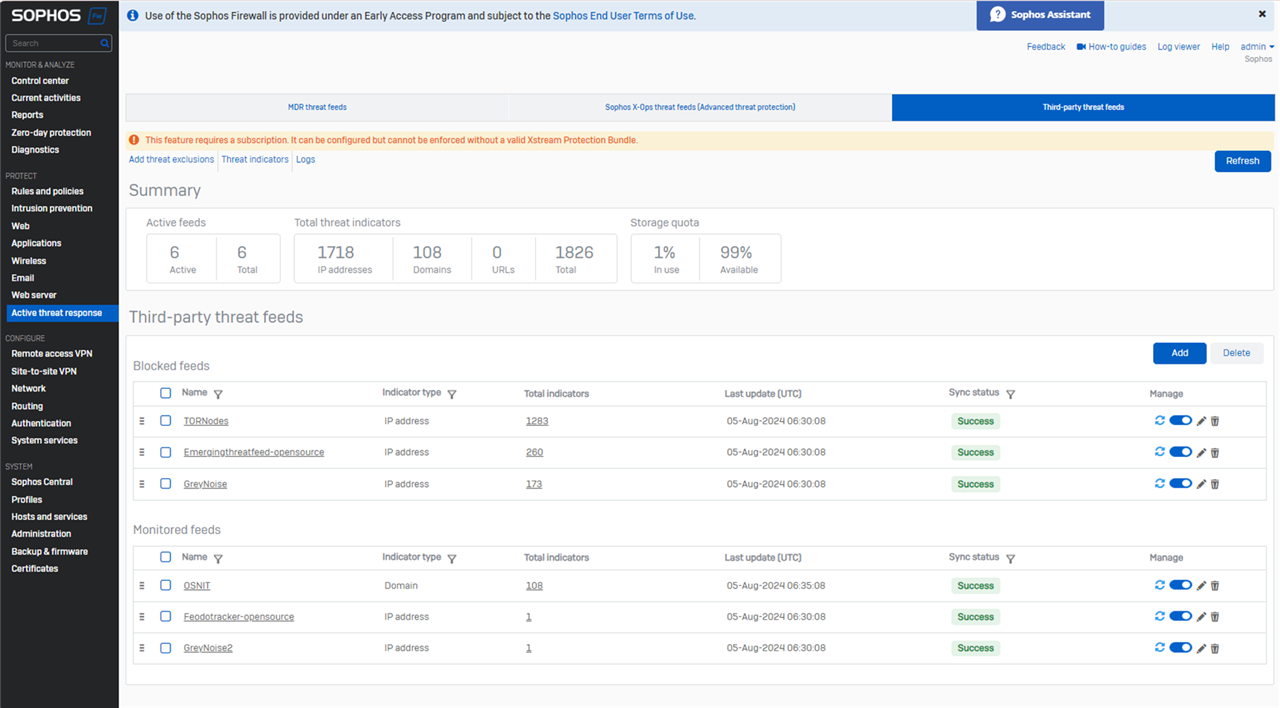
Setup and monitor your third-party threat feeds under the Active Threat Response menu
- Synchronized Security’s automated response to active threats is also extended to third-party threat feeds. Firewall presents threat analysis after corelating threat attempts with managed endpoint.
Format
[bearbeitet von: LuCar Toni um 7:53 AM (GMT -7) am 30 Aug 2024]

