Hi folks,
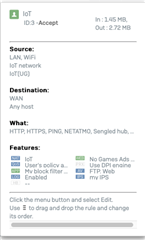
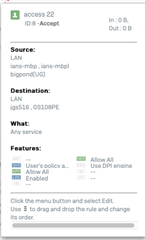
while working on a thread in the XG forum I checked some of firewall settings and found I think that the DPI is on by default.The screenshots below do not show the DPI as highlighted, on the rules where it is selected and not selected.
Ian
The first screenshot uses the DPI and where as the second screenshot is of an internal connection.
Am I interpreting the screenshots wrong or is there a bug?