Hello Sophos community,
I am trying to set up a szenario where I have to send IPsec Remote access traffic through a Site-to-Site IPsec VPN with 1:n NAT translation on a XGS Firewall.
It seems to work on UTM: Sending Remote access traffic through Site-to-site VPN, with 1:1 nat translation
It did work on Cisco ASA, that I retired and that I have replaced with the XGS.
Setup:
Remote User -(IPsec Remote Access VPN)-> Sophos XGS -(IPSEC Site-to-site VPN)-> Partner servers
We have a requirement for remote users (Sophos Connect Client) to access partners servers. Our IPsec Remote Access VPN is on a VPN subnet (192.168.99.0/24), internal LAN is 192.168.1.0/24
Our partner has the requirement that traffic is sent from the 1.2.3.4 IP (1:n NAT) to his networks.
The site-to-site VPN (Tunnel: To_Partner) is established and working, showing up at both ends. Local network on my end is set to be 1.2.3.4 - no NAT in Site-to-Site VPN active.
I have set up "system ipsec_route add net 10.1.1.0/255.255.255.0 tunnelname To_Partner"
Found this command mentioned here: support.sophos.com/.../KB-000037043
I have created a NAT rule (Name: NAT-Partner) to change traffic from internal LAN 192.168.1.0 as well as RA VPN LAN 192.168.99.0/24 , going to partner network 10.1.1.0, to map the source as 1.2.3.4
Firewall rules have been set up for both the S2S VPN, and internal LAN as well as RA VPN LAN
.
I have added the Partner network to the local networks section in the IPsec Remote Access VPN setup.
Problem: I can ping as well as access partner network servers' ressources from internal LAN 192.168.1.0
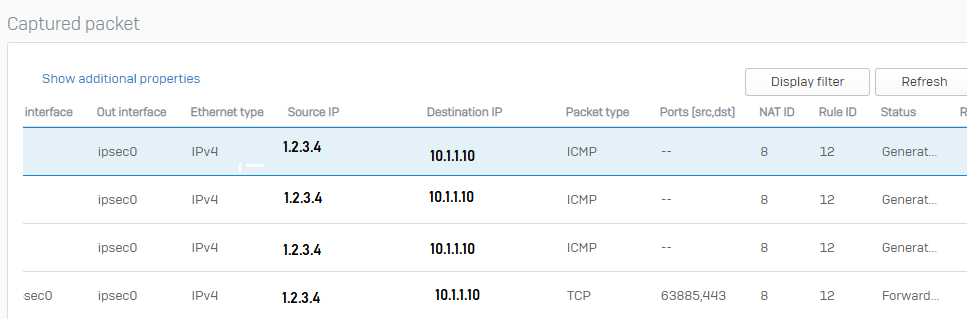
I can ping from RA VPN LAN. I am, however, unable to access partner server's remote ressources.
When trying to access a partner servers ressources from the RA VPN LAN, the counter on the NAT rule "NAT-Partner" increases. Sophos packet tracers says: Invalid traffic
I tried an "any"-"any" firewall rule. No success so far.
Do I have to put the Cisco ASA5510 back in place? I am a bit lost.
Cheers,
XGS admin
This thread was automatically locked due to age.