So I attempted to get the application control working based on this article: https://community.sophos.com/sophos-xg-firewall/f/recommended-reads/120242/sophos-xg-firewall-how-to-create-an-exception-in-application-filter but I could not get this to work.
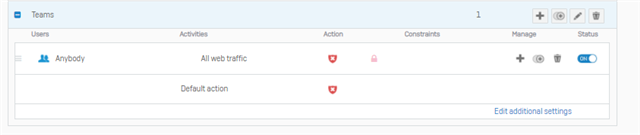
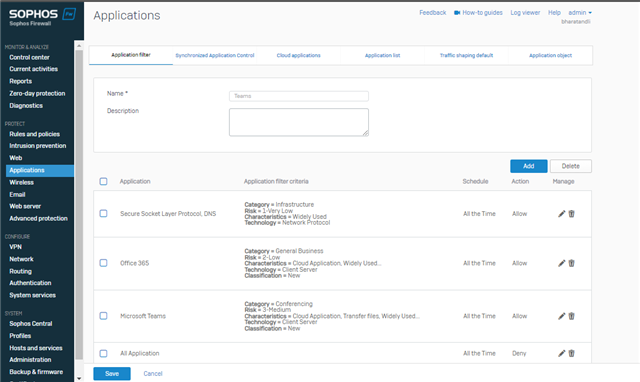
We have a application from Honeywell that uses multiple outgoing ports, hundreds of them with no set port range, that we need to allow outgoing access. The application is correctly detected by Synchronized Application Control and I customized it with the full name and categorized it as general business. I then made a Application Filter with that application in it and allowed then saved it. Then I made a new firewall rule for it for LAN - All -> WAN - All - All Services and under the application control I put it in. But the rule is allowing everything outgoing now.
How do I make a firewall rule allowing this application full outgoing ports without allowing anything else?
This thread was automatically locked due to age.