Reworked overview of my part - We are working now 2 weeks on the Sophos Switch to get it configured to apply to our customer situation:
Still existing problems:
- Can only create 3 L3 vlan interfaces with IP addresses after we see this error:
RT-DE010001(config)# int vlan 20
RT-DE010001(config-if)# ip add
RT-DE010001(config-if)# ip address 10.30.20.1 255.255.255.0
RT-DE010001(config)# int vlan 30
% No free interfaces are available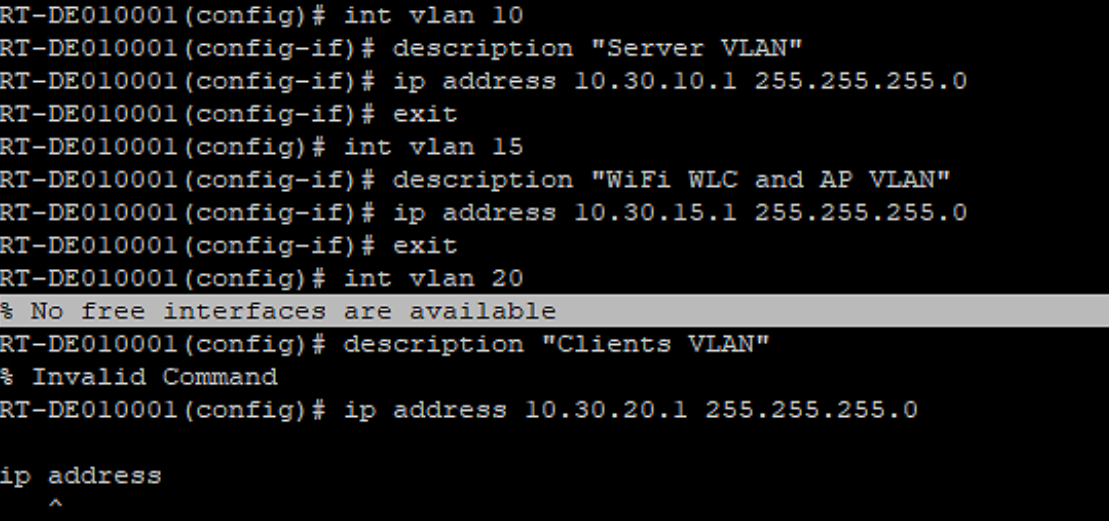
- We also cannot get the Switch enabled for routing traffic between the L3 interfaces
- Bad Block error on switch startup
Turn On Serdes
Mac_Polling_PHY Config
Enable PHY Polling
Misc
PHY init (unit 0)
Mgmt_dev init (unit 0)
Enter Esc key to stop autoboot: 0
## Booting image from partition ... 1
Skipping bad block 0x06220000 <-------------------------------- ERROR ????
## Booting kernel from Legacy Image at 81000000 ...
Image Name: IMG-01.0.0754
Created: 2021-11-25 8:30:39 UTC
Image Type: MIPS Linux Kernel Image (lzma compressed)
Data Size: 20264466 Bytes = 19.3 MB
Current Switch:
Model: CS110-24FP
Firmware Version : 01.0.0754
Logging Option : Console Logging
Login Authentication Mode : Local
Config Save Status : Successful
Remote Save Status : Not Initiated
Config Restore Status : Successful
Traffic Separation Control : none
Loader Version : 03.02.01
Protocol Version : 3.02.243a
Hardware Version : 1.0.0
Here is my sequence until i run into the error/problem - hopefully some can give us any hint on it:
Reset Switch
restore-defaults
Note: Reset also to default password (Sticker backside)
Script Block 1 General system settings
conf t
system name "RT-DE010001"
system contact "Martin Mustermanr"
system location "Germany Aachen"
set system description "Sophos CS110-24FP"
set switch-name RT-DE010001
username admin password Passw0rd! confirm-password Passw0rd! privilege 15
Script Block 2 - Create the Vlans and assign the Ports
vlan 1
ports name Management
exit
vlan 10
ports name Server
exit
vlan 11
ports name VoicePbx
exit
vlan 15
ports name WlcAccessPoints
exit
vlan 20
ports name Clients
ports add gigabitethernet 0/23 untagged gigabitethernet 0/23
exit
vlan 30
ports name Printer
exit
vlan 99
ports name TransferToFirewall
ports add gigabitethernet 0/1 untagged gigabitethernet 0/1
ports add gigabitethernet 0/7 untagged gigabitethernet 0/7
exit
vlan 998
ports name FirewallHa
ports add gigabitethernet 0/5 untagged gigabitethernet 0/5
ports add gigabitethernet 0/11 untagged gigabitethernet 0/11
exit
vlan 999
ports name WAN
ports add gigabitethernet 0/3 untagged gigabitethernet 0/3
ports add gigabitethernet 0/9 untagged gigabitethernet 0/9
ports add gigabitethernet 0/17 untagged gigabitethernet 0/17
exit
Script Block 3 - Setup Management VLAN with IP
int vlan 1
description "Management VLAN"
#to switch to static ip remove in config file: ip address dhcp -> ERROR: % Address allocation method must be manual to configure IP Address
no ip address
ip address 10.30.0.1 255.255.255.0
exit
Note: If you not stop here and wait you will see errors like this:
#RT-DE010001(config)# int vlan 99
#RT-DE010001(config-if)# description "Transfer to Firewall VLAN"
#RT-DE010001(config-if)# ip address 10.99.30.1 255.255.255.0
#% Invalid SubnetMask For the Given Ipaddress
# after waiting same command works suddenly !
Script Block 4 - Add more L3 vlan interfaces with IP
int vlan 99
description "Transfer to Firewall VLAN"
ip address 10.99.30.1 255.255.255.0
exit
int vlan 10
description "Server VLAN"
ip address 10.30.10.1 255.255.255.0
exit
int vlan 15
description "WiFi WLC and AP VLAN"
ip address 10.30.15.1 255.255.255.0
exit
int vlan 20
description "Clients VLAN"
ip address 10.30.20.1 255.255.255.0
ERROR --> % No free interfaces are available
After adding the 4th vlan interface we always face this error message - same to local Web UI !
Script planned to finish configuration L3 interfaces but impossible:
int vlan 20
description "Clients VLAN"
ip address 10.30.20.1 255.255.255.0
exit
int vlan 21
description "Clients VLAN"
ip address 10.30.21.1 255.255.255.0
exit
int vlan 22
description "Clients VLAN"
ip address 10.30.22.1 255.255.255.0
exit
int vlan 30
description "Printer VLAN"
ip address 10.30.30.1 255.255.255.0
exit
Script Block to finish port setup
int gigabitethernet 0/1
description "Sophos A Lan"
switchport pvid 99
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/7
description "Sophos B Lan"
switchport pvid 99
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/5
description "Sophos A HA"
switchport pvid 998
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/11
description "Sophos B HA"
switchport pvid 998
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/3
description "Sophos A WAN"
switchport pvid 999
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/9
description "Sophos B WAN"
switchport pvid 999
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/17
description "Router WAN"
switchport pvid 999
switchport acceptable-frame-type all
switchport ingress-filter
exit
int gigabitethernet 0/23
description "Laptop Client Network"
switchport pvid 20
switchport acceptable-frame-type all
switchport ingress-filter
exit
# Route to actve Sophos HA LAN interface
ip route 0.0.0.0 0.0.0.0 10.99.30.254
exit
save
We have also opened a ticket and also escalate it but from Sophos until now only unqualified replies!
I am wondering that in this Switch section only people are reviewing but it looks to me most are also try to understand the product !
I also hope we can exchange here more experience with the switches
Updated TAGs
[edited by: Erick Jan at 5:47 AM (GMT -8) on 11 Jan 2024]

