Hi,
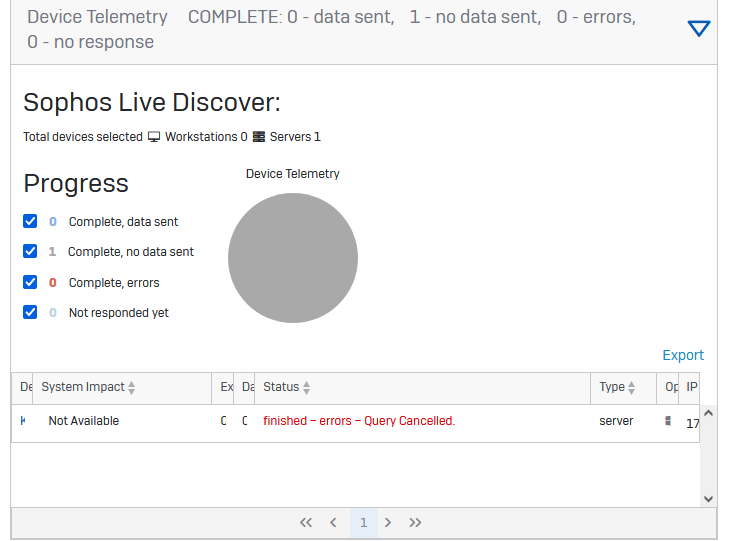
I need this Live Response quickly, unfortunately Sophos Intercept X is aborting the Query.
What is this and how do I get to my data? I just want to use that product with a default query!
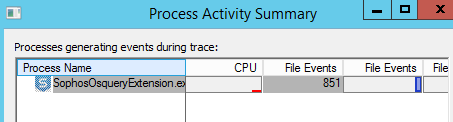
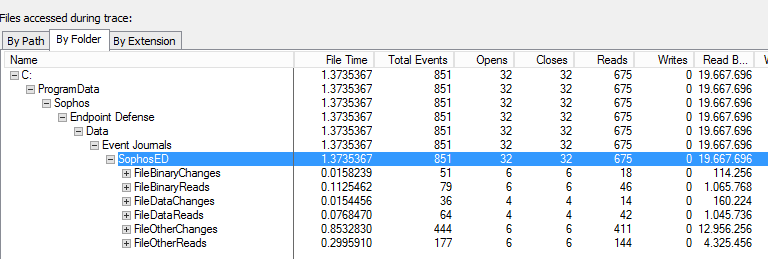
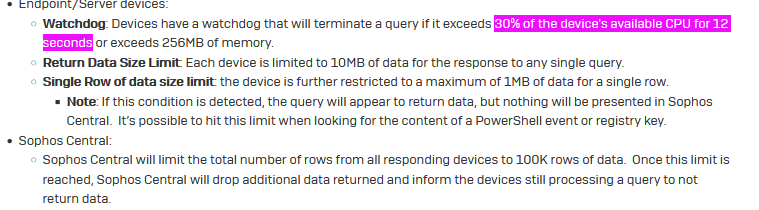
2022-03-31T14:29:22.937Z [ 9644: 8204] E Process SophosOsqueryExtension.exe exceeded 30% CPU limit for over: 9 counts
2022-03-31T14:29:22.946Z [ 9644: 6484] W Query Cancelled
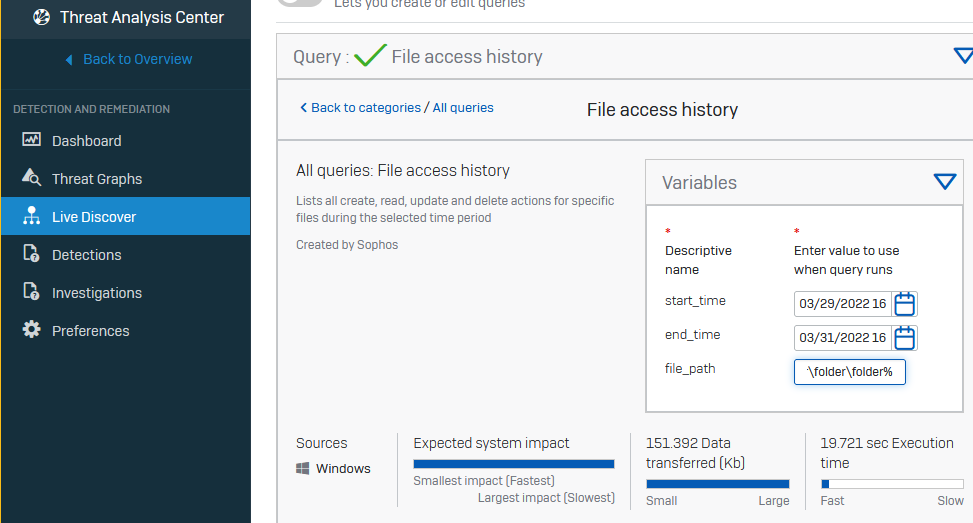
2022-03-31T14:28:37.916Z [ 9644: 8204] I Starting FileProcessor: C:\ProgramData\Sophos\Live Query\Queries\Incoming
2022-03-31T14:29:12.534Z [ 9644: 6484] I Running LiveQuery: correlationId:29652b93-474f-41a7-8531-c7104b733871 requestJson:{"name":"File access history","query":"SELECT \n STRFTIME('%Y-%m-%dT%H:%M:%SZ', DATETIME(file_journal.time,'unixepoch')) AS date_time,\n process_journal.processName AS process_name,\n CASE file_journal.eventType\n WHEN 0 THEN 'Created'\n WHEN 1 THEN 'Renamed'\n WHEN 2 THEN 'Deleted'\n WHEN 3 THEN 'Modified'\n WHEN 4 THEN 'HardLink Created'\n WHEN 5 THEN 'Timestamps Modified'\n WHEN 6 THEN 'Permissions Modified'\n WHEN 7 THEN 'Ownership Modified'\n WHEN 8 THEN 'Accessed'\n WHEN 9 THEN 'Binary File Mapped'\n END AS event_type,\n REPLACE(file_journal.pathname, RTRIM(file_journal.pathname, REPLACE(file_journal.pathname, '\\', '')), '') AS file_name,\n process_journal.pathname AS process_path,\n file_journal.pathname AS file_path,\n file_journal.sophosPID AS sophos_pid,\n process_journal.sha256 AS sha256,\n process_properties.mlScore AS ml_score,\n process_properties.puaScore AS pua_score,\n process_properties.localRep AS local_rep,\n process_properties.globalRep AS global_rep\nFROM sophos_file_journal AS file_journal\nLEFT JOIN sophos_process_journal AS process_journal\n ON process_journal.sophosPID = file_journal.sophosPID\n AND process_journal.time = REPLACE(file_journal.sophosPID, RTRIM(file_journal.sophosPID, REPLACE(file_journal.sophosPID , ':', '')), '') / 10000000 - 11644473600\nLEFT JOIN sophos_process_properties AS process_properties \n USING (sophosPID)\nWHERE\n file_journal.pathname LIKE 'F:\\Folder\\Folder\\Folder%'\n AND file_journal.time > 1648563081\n AND file_journal.time < 1648735200\nORDER BY file_journal.time DESC","type":"sophos.mgt.action.RunLiveQuery"}
2022-03-31T14:29:22.937Z [ 9644: 8204] E Process SophosOsqueryExtension.exe exceeded 30% CPU limit for over: 9 counts
2022-03-31T14:29:22.943Z [ 9644: 8204] I Stopping FileProcessor: C:\ProgramData\Sophos\Live Query\Queries\Incoming
2022-03-31T14:29:22.943Z [ 9644: 8204] I Stopping process SophosOsquery.exe
2022-03-31T14:29:22.946Z [ 9644: 6484] W Query Cancelled
This thread was automatically locked due to age.