How does EndPoint Protection / Intercept X react to Social Engineering Invasive Pop-ups?
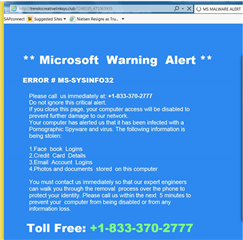
We had an associate that was on one web site, trying to download an Invoice, when an invasive pop-up showed up (repeated if the pop-up was closed by the 'x', using the Task bar close option, or using End Task). The pop-up is what you see below.
The pop-up was moveable, so I was able to identify the website as trendocreativelinksys.club
Sophos didn't prevent the pop-up. Thankfully, the associate knew enough to contact IS. I took screen shots, started a virus scan, and killed the IE tasks successfully. I also added another Tag, named it Social Engineering, and added that to a block in Control sites tagged in Website Management within our New Hacking Prevention Policy.
My question is mostly, is that how it should work, for first-time visits to this type of web site?
This thread was automatically locked due to age.