Hello Team,
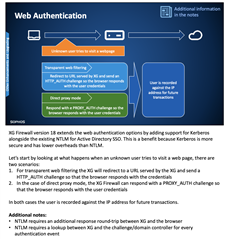
I was going through this new feature implementation i.e. kerberos authentication in which I have notice few things after configuration that I would like to clarify:-
1) If we configure browser based proxy with device Hostname then it is going through Kerberos authentication and we are getting AD-SSO Kerberos in live user page
2) If we configure browser based proxy with IP address then it is going through NTLM authentication and we are getting AD-SSO NTLM in live user page
3) For transparent connection in which I am not configuring any thing in browser proxy then by default it is taking AD-SSO NTLM and not kerberos
Is this above details are as in known behavior or am I missing something?