Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This article describes how to configure a site-to-site IPsec PBVPN tunnel between the Sophos Firewall and SonicWall firewall using a pre-shared key to authenticate VPN peers.
Table of Contents
Product and Environment
- Sophos Firewall
- SonicWall version SonicOS 7.0.0-R906
Prerequisites
You must have read-write permissions on the SFOS web admin and SonicWall web admin for the relevant features.
Network diagram
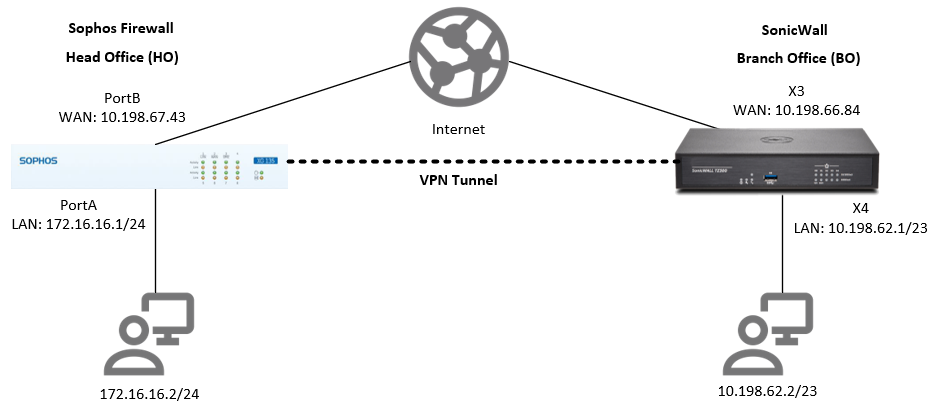
Configuration
Sophos Firewall
Create local and remote LAN
- Go to Hosts and services > IP host and click Add.
- Configure the local and remote LAN using the following values and click Save for each configuration.
Local LAN
Parameter Value Name Enter a name.
Ex. XG_LANIP version IPv4 Type Network IP address Enter local LAN network IP address.
Ex. 172.16.16.0Subnet Select local LAN subnet.
Ex. /24 (255.255.255.0)
Remote LAN
Parameter Value Name Enter a name.
Ex. SonicWall_LANIP version IPv4 Type Network IP address Enter remote LAN network IP address.
Ex. 10.198.62.0Subnet Select remote LAN subnet.
Ex. /23 (255.255.254.0)
Create IPsec profile
- Go to Profiles > IPsec profiles and click Add.
- Configure the following:
Parameter Value General settings Name Enter a name.
Ex. XG IPsec PolicyKey exchange IKEv2 Authentication mode Main mode Key negotiation tries 0 Re-key connection Turned on Phase 1 Key life 28800 Re-key margin 360 Randomize re-keying margin by 100 DH group (key group) 14 (DH2048) Encryption AES256 Authentication SHA2 512 Phase 2 PFS group (DH group) 14 (DH2048) Key life 3900 Encryption AES256 Authentication SHA2 512 Dead Peer Detection Dead Peer Detection Turned on Check peer after every 30 Wait for response up to 120 When peer unreachable Re-initiate - Click Save.
Create IPsec connection
- Go to Site-to-site VPN > IPsec and click Add.
- Configure the following:
Parameter Value General settings Name Enter a name.
Ex. XG_to_SonicWallIP version IPv4 Connection type Site-to-site Gateway type Respond only Activate on save Turned on Create firewall rule Turned on Encryption Profile Select the IPsec profile you created earlier.
Ex. XG IPsec PolicyAuthentication type Preshared key Preshared key Enter a preshared key. Repeat preshared key Repeat the preshared key. Gateway settings Listening interface Select your WAN port/IP address.
Ex. PortB – 10.198.67.43Local subnet Select the local LAN that you created earlier.
Ex. XG_LANGateway address Enter the remote WAN IP address.
Ex. 10.198.66.84Remote subnet Select the remote LAN that you created earlier.
Ex. SonicWall_LANAdvanced User authentication mode None - Click Save. The IPsec connection is automatically activated and an automatic firewall rule is also created.
SonicWall
Create Address Object
- Go to Object > Addresses and click Add.
- Configure the local and remote LAN using the following values and click OK for each configuration.
Local LAN
Parameter Value Name Enter a name.
Ex. SonicWall_LANZone Assignment VPN Type Network Network Enter local LAN network IP address.
Ex. 10.198.62.0Netmask/Prefix Length Enter local LAN netmask.
Ex. 255.255.254.0
Remote LAN
Parameter Value Name Enter a name.
Ex. XG_LANZone Assignment VPN Type Network Network Enter remote LAN network IP address.
Ex. 172.16.16.0Netmask/Prefix Length Enter remote LAN netmask.
Ex. 255.255.255.0
Turn on VPN
- Go to Network > IPsec VPN > Rules and Settings > Settings.
- Turn on Enable VPN.
- Go to System > Administration > Firewall Name and enter a value in Unique Firewall Identifier.
Create VPN policies
- Go to Network > IPsec VPN > Rules and Settings > Policies and click Add.
- In the General tab, configure the following:
Parameter Value Security Policy Policy Type Site to Site Authentication Method IKE using Preshared Secret Name Enter a name.
Ex. Tunnel to XG FirewallIPsec Primary Gateway Name or Address Enter the local WAN IP address
Ex. 10.198.67.43IPsec Secondary Gateway Name or Address 0.0.0.0 IKE Authentication Shared Secret Enter the same preshared key configured in Sophos Firewall. Confirm Shared Secret Repeat the preshared key. Local IKE ID IPv4 Address Peer IKE ID IPv4 Address - In the Network tab, configure the following:
Parameter Value Local Networks Choose local network from list Select the local LAN that you created earlier.
Ex. SonicWall_LANRemote Networks Choose destination network from list Select the remote LAN that you created earlier.
Ex. XG_LAN - In the Proposals tab, configure the following:
Parameter Value IKE (Phase 1) Proposal Exchange IKEv2 Mode DH Group Group 14 Encryption AES256 Authentication SHA512 Life Time (seconds) 26000 Ipsec (Phase 2) Proposal Protocol ESP Encryption AES256 Authentication SHA512 Enable Perfect Forward Secrecy Turned on DH Group Group 14 Life Time (seconds) 3800
Note: Phase 1 and phase 2 Life Time are configured with slightly lower values on SonicWall since it is the initiator. This will avoid re-key collisions. - In the Advanced tab, configure the following:
Parameter Value Enable Keep Alive Turned on
This setting makes SonicWall as the initiator of the IPsec tunnel.Enable Windows Networking (NetBIOS) Broadcast Turned on WXA Group None Default LAN Gateway (optional) 0.0.0.0 VPN Policy bound to The WAN interface.
Ex. Interface X3
- Click OK.
Check packet filter rules
This is automatically added. To verify, go to Policy > Access Rules, click the Matrix icon, and chose VPN to LAN or LAN to VPN.
Activate the connection
Sophos Firewall
- Go to Site-to-site VPN > IPsec.
- Click the red button under Connection and click OK to establish the connection.
- The button should turn green, indicating that the connection is established.
SonicWall
- Go to VPN > Settings > VPN Policies.
- Select the connection and click Add.
- Make sure the tunnel is enabled in the Policies tab and that it shows under the Active Tunnels tab.
Verification
Run a ping test from the client behind Sophos Firewall to the client behind Sonicwall.
Example:
From the client behind Sophos Firewall, ping 10.198.62.2. These packets should go through the IPsec tunnel. This can be verified by running tcpdump -n esp on the Sophos Firewall console.
Fixed Spacing Last update by DominicRemigio Added SonicOS version and updated "VPN Policy bound to" to use the WAN interface
[edited by: Erick Jan at 2:39 AM (GMT -8) on 15 Nov 2023]

