I'm trying to set something up where I have a rule for a particular device on my LAN that will reject all traffic from that device to the internet (WAN on my XG), but then be able to define allow rules to sit above it in the rule list so that I can open up certain services. The problem is that even without the "reject" rule in place, the "accept" rule breaks communication! I'm so confused.
With the accept rule enabled, I can see packets go out through the rule in the logs, but nothing comes back. If I disable the accept rule, then communication works fine. What am I doing wrong??
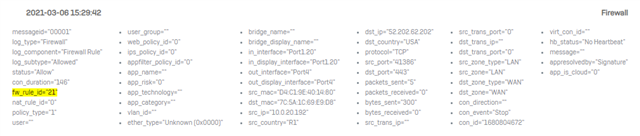
From the log (shows 0 packets received):
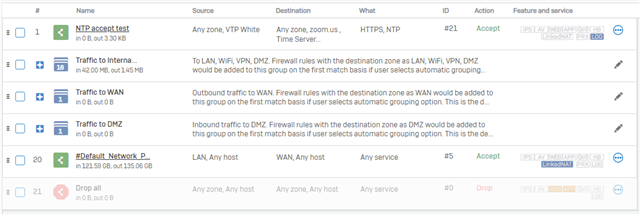
Rule list:
Rule configuration:
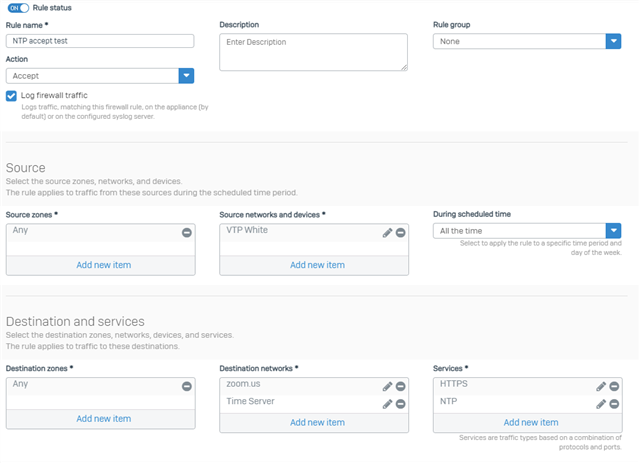
To test, I'm trying to get to zoom.us from the "VTP White" device. I previously had the source zone set as LAN and destination zone as WAN, but changing them to Any/Any didn't change anything.
This thread was automatically locked due to age.


