Hi,
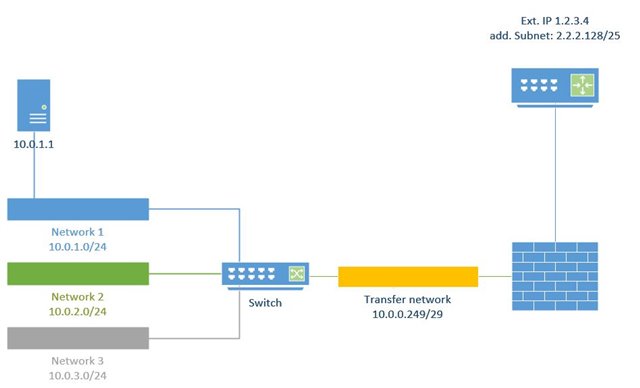
a new customer actually has a watchguard firewall. The watchguard is replaced by a AP-cluster of 2 XG330.
He has a normal WAN connection with a static IP and, additionally a /25 subnet (completely other range) that is routed to the WAN-IP. On the watchguard there is a simple 1:1 NAT rule that maps the external subnet to an internal subnet (not the full /24, only the first half of it) and this works inbound as outbound.
I first configured 126 additional IPs on the WAN interface (what a pain and the IPs are totally mixed up, really great for seeing if you got all IPs covered...) and now am a bit struggeling with the NAT rules.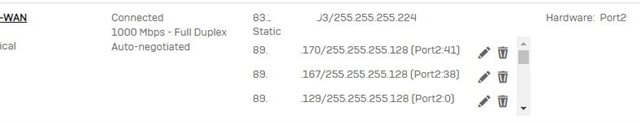
As I found out by searching the forum the XG is not able to NAT subnets, only ranges (really, Sophos?) and I managed to create the 1:1 DNAT rule from WAN to LAN with "one to one" loadbalancing.
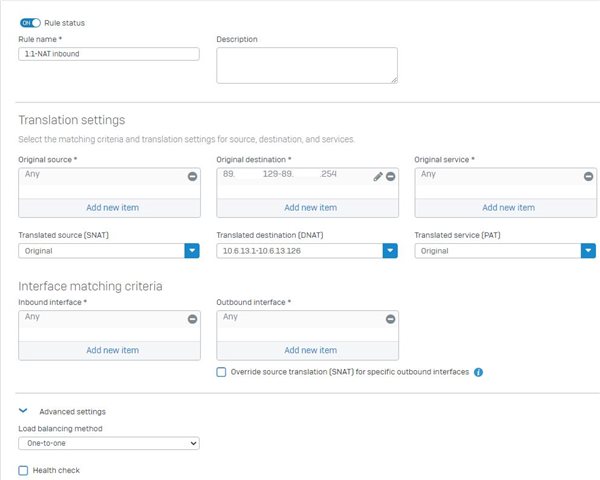
But how do I create the SNAT rule? I selected the internal range as source and the external range as SNAT object, but "one to one" loadbalancing doesn't seem to apply here.
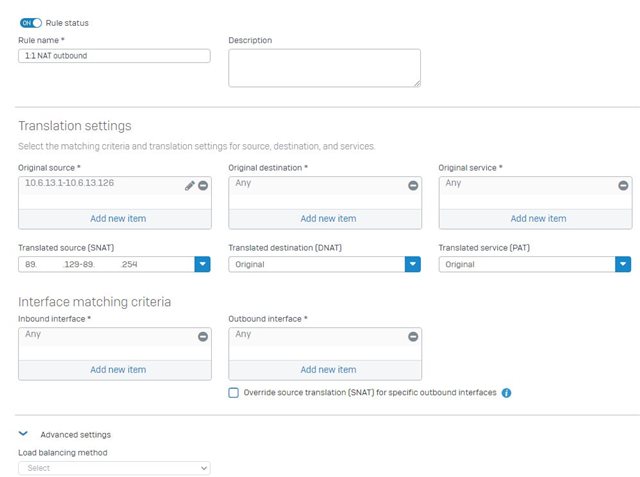
Another point where I am unsure is the "Override source translation" part.
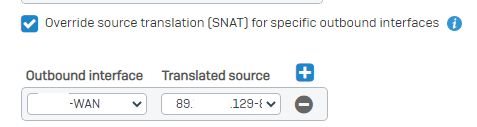
Or am I completely on the wrong way to configure this?
This thread was automatically locked due to age.