I am looking to secure my internal network with the IoT devices.
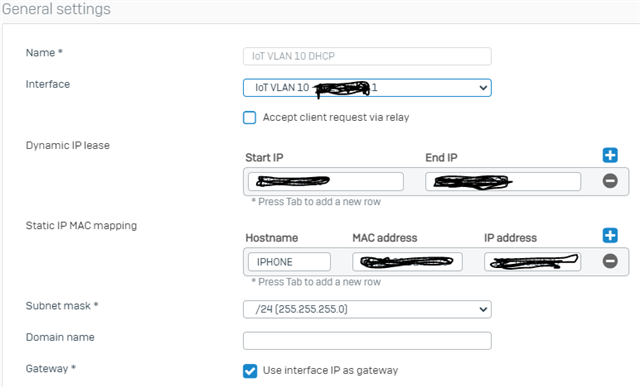
Currently I have a home automation system that controls the IoT devices. There are 20+ devices. Each device has a static IP based on the MAC ID setup in XG.
Current Setup:
Modem <> Sophos XG v18 <> Switch <> WiFi via Unifi AP's.
Network PC with VM (home automation) & Plex server (this PC is wired)
NAS (wired)
Have 5 security cameras (wired)
My goal is to secure the wireless IoT devices as well as the security cameras.
I need the home automation (VM) to be able to contact the IoT devices. The NAS controls the security cameras so this also needs to have contact with the cameras.
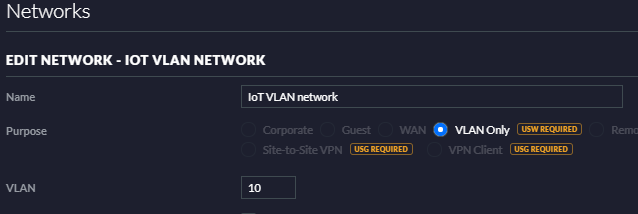
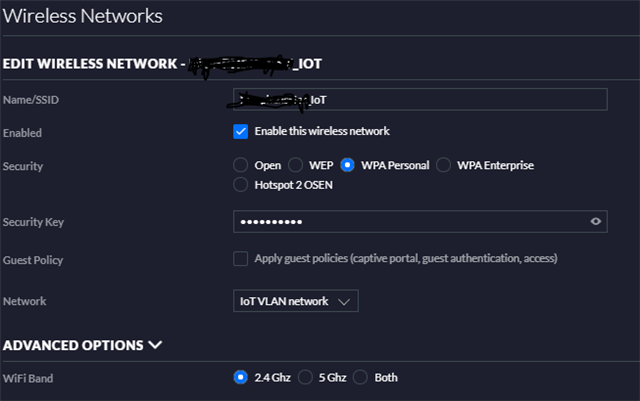
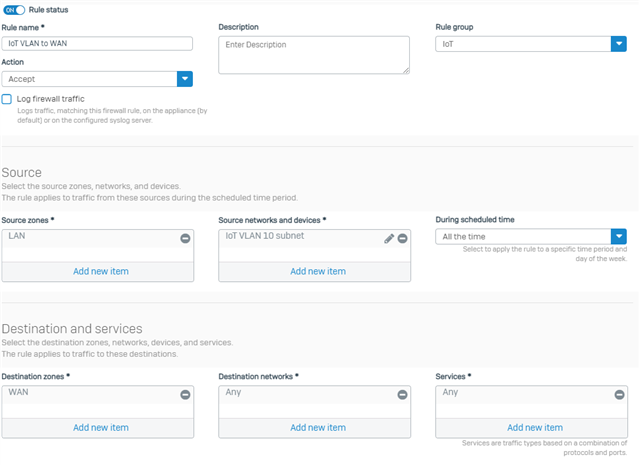
I have seen some posts on setting up a WiFi for the IoT devices and creating some VLANs. I have also seen some posts on using the MAC IDs to do some policies/filtering. Looking for the easiest and best practice to secure.
Thanks
This thread was automatically locked due to age.