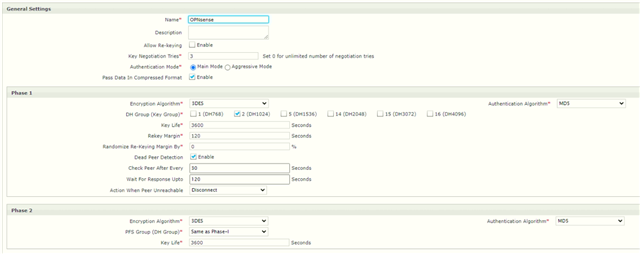
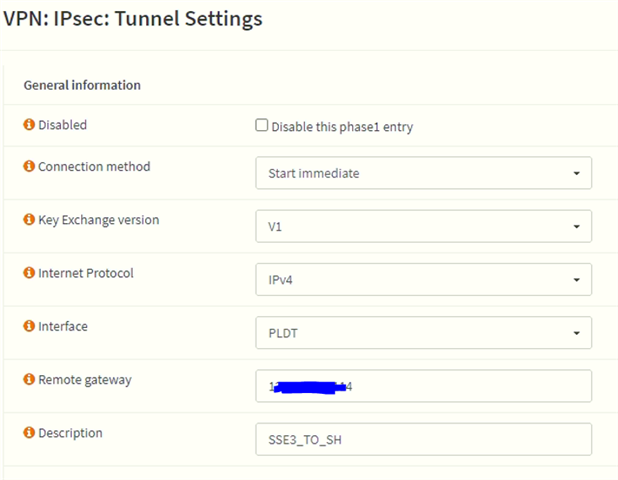
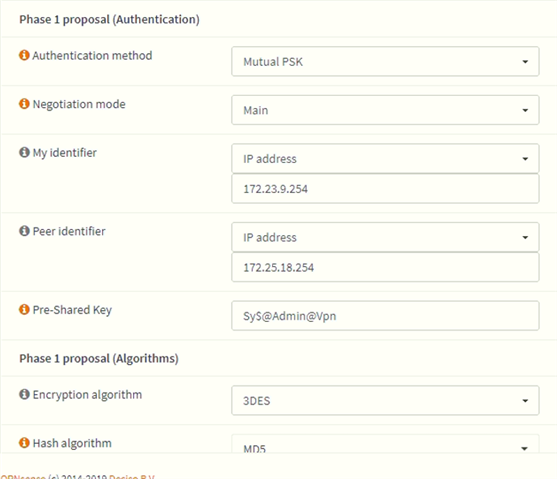
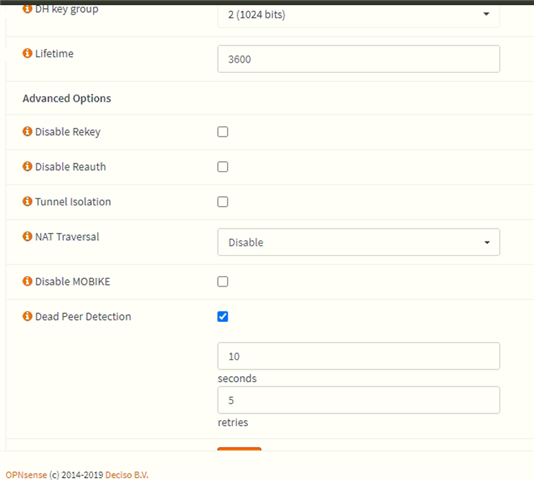
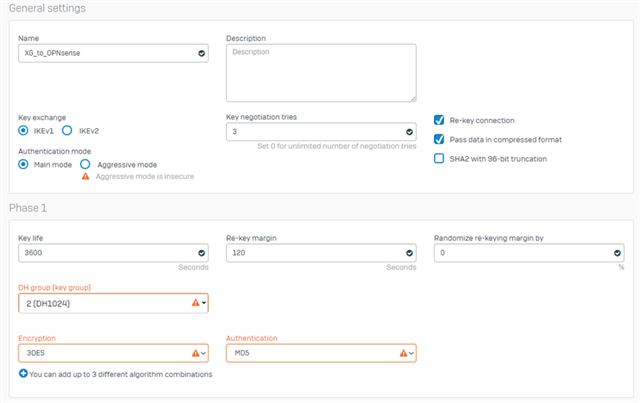
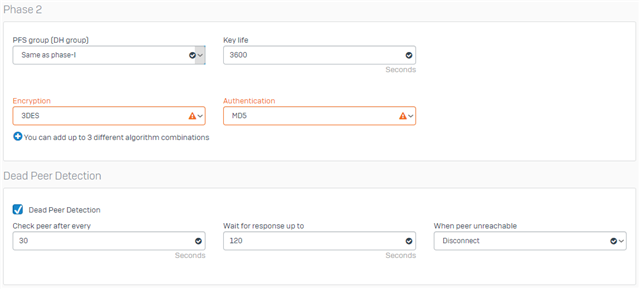
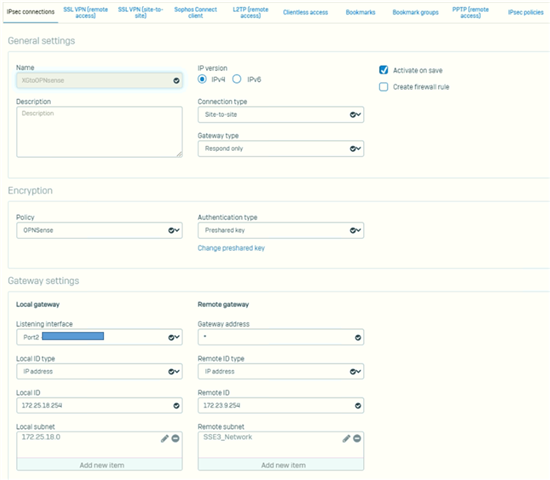
We have existing Cyberoam in our HQ. One of our store is using OPNsense. Currently our HQ and the branch office is connected via IPSec VPN of Cyberoam and OPNSense. Now I bought a new XG. Im trying to establish IPSec VPN between XG and OPNSense but it can't connect. I check the logs of strongswan and charon.
``````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````
XG135_XN03_SFOS 17.5.14 MR-14-1# tail -f /log/Charon.log
tail: can't open '/log/Charon.log': No such file or directory
tail: no files
XG135_XN03_SFOS 17.5.14 MR-14-1# tail -f /log/charon.log
2021-01-11 20:25:23 14[IKE] <XGtoOPNsense-1|1> ### queue_child invoking quick_mo
de_create
2021-01-11 20:25:23 14[IKE] <XGtoOPNsense-1|1> ### quick_mode_create: 0x7fd5c800
0e60 config 0x7fd5900025f0
2021-01-11 20:25:23 14[IKE] <XGtoOPNsense-1|1> found queued QUICK_MODE task with
identical child config
2021-01-11 20:25:23 14[IKE] <XGtoOPNsense-1|1> ### destroy: 0x7fd5780028a0
2021-01-11 20:25:24 27[CFG] rereading secrets
2021-01-11 20:25:24 27[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:25:24 27[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:25:24 27[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:25:24 27[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:25:24 30[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:25:30 19[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:25:30 18[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:25:30 31[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:25:30 21[KNL] interface Port2_ppp activated
2021-01-11 20:25:30 25[KNL] interface Port2_ppp deactivated
2021-01-11 20:25:30 16[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:25:33 24[KNL] interface Port2_ppp deleted
2021-01-11 20:25:35 08[CFG] rereading secrets
2021-01-11 20:25:35 08[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:25:35 08[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:25:35 08[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:25:35 08[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:25:36 28[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:25:36 14[CFG] vici initiate 'XGtoOPNsense-1'
2021-01-11 20:25:36 06[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
2021-01-11 20:25:36 06[IKE] <XGtoOPNsense-1|1> ### queue_child invoking quick_mo
de_create
2021-01-11 20:25:36 06[IKE] <XGtoOPNsense-1|1> ### quick_mode_create: 0x226a1f0
config 0x7fd5900025f0
2021-01-11 20:25:36 06[IKE] <XGtoOPNsense-1|1> found queued QUICK_MODE task with
identical child config
2021-01-11 20:25:36 06[IKE] <XGtoOPNsense-1|1> ### destroy: 0x7fd5c8000e60
2021-01-11 20:25:42 24[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:25:42 29[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:25:42 18[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:25:42 19[KNL] interface Port2_ppp activated
2021-01-11 20:25:42 20[KNL] interface Port2_ppp deactivated
2021-01-11 20:25:42 21[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:25:43 07[CFG] rereading secrets
2021-01-11 20:25:43 07[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:25:43 07[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:25:43 07[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:25:43 07[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:25:43 04[CFG] vici initiate 'XGtoOPNsense-1'
2021-01-11 20:25:43 20[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````````
XG135_XN03_SFOS 17.5.14 MR-14-1# tail -f /log/strongswan.log
2021-01-11 20:21:44 30[IKE] <XGtoOPNsense-1|1> found queued QUICK_MODE task with
identical child config
2021-01-11 20:21:44 30[IKE] <XGtoOPNsense-1|1> ### destroy: 0x7fd580000d20
2021-01-11 20:21:44 24[KNL] interface Port2_ppp deleted
2021-01-11 20:21:44 07[CFG] rereading secrets
2021-01-11 20:21:44 07[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:21:44 07[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:21:44 07[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:21:44 07[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:21:45 27[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:21:47 08[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
2021-01-11 20:21:52 32[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:21:52 21[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:21:52 14[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:21:52 28[KNL] interface Port2_ppp activated
2021-01-11 20:21:52 16[KNL] interface Port2_ppp deactivated
2021-01-11 20:21:52 24[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:21:54 07[CFG] rereading secrets
2021-01-11 20:21:54 07[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:21:54 07[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:21:54 07[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:21:54 07[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:21:54 06[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:21:54 13[CFG] vici initiate 'XGtoOPNsense-1'
2021-01-11 20:21:54 03[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
2021-01-11 20:21:54 03[IKE] <XGtoOPNsense-1|1> ### queue_child invoking quick_mo
de_create
2021-01-11 20:21:54 03[IKE] <XGtoOPNsense-1|1> ### quick_mode_create: 0x7fd55c00
16f0 config 0x7fd5900025f0
2021-01-11 20:21:54 03[IKE] <XGtoOPNsense-1|1> found queued QUICK_MODE task with
identical child config
2021-01-11 20:21:54 03[IKE] <XGtoOPNsense-1|1> ### destroy: 0x7fd584001140
2021-01-11 20:21:56 05[KNL] interface Port2_ppp deleted
2021-01-11 20:22:03 18[CFG] rereading secrets
2021-01-11 20:22:03 18[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:22:03 18[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:22:03 18[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:22:03 18[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:22:03 25[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:22:03 22[CFG] vici initiate 'XGtoOPNsense-1'
2021-01-11 20:22:03 15[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
2021-01-11 20:22:03 15[IKE] <XGtoOPNsense-1|1> ### queue_child invoking quick_mo
de_create
2021-01-11 20:22:03 15[IKE] <XGtoOPNsense-1|1> ### quick_mode_create: 0x7fd58000
0cf0 config 0x7fd5900025f0
2021-01-11 20:22:03 15[IKE] <XGtoOPNsense-1|1> found queued QUICK_MODE task with
identical child config
2021-01-11 20:22:03 15[IKE] <XGtoOPNsense-1|1> ### destroy: 0x7fd55c0016f0
2021-01-11 20:22:04 32[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:22:04 17[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:22:04 24[CFG] rereading secrets
2021-01-11 20:22:04 24[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:22:04 24[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:22:04 24[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:22:04 24[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:22:04 03[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:22:04 20[KNL] interface Port2_ppp activated
2021-01-11 20:22:04 05[KNL] interface Port2_ppp deactivated
2021-01-11 20:22:04 28[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:22:04 27[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:22:07 30[KNL] interface Port2_ppp deleted
2021-01-11 20:22:15 28[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:22:15 25[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
2021-01-11 20:22:15 27[KNL] 124.1XX.4X.1XX appeared on Port2_ppp
2021-01-11 20:22:15 08[KNL] interface Port2_ppp activated
2021-01-11 20:22:15 24[KNL] interface Port2_ppp deactivated
2021-01-11 20:22:15 20[KNL] 124.1XX.4X.1XX disappeared from Port2_ppp
^A2021-01-11 20:22:18 26[KNL] interface Port2_ppp deleted
2021-01-11 20:22:22 22[CFG] rereading secrets
2021-01-11 20:22:22 22[CFG] loading secrets from '/_conf/ipsec/ipsec.secrets'
2021-01-11 20:22:22 22[CFG] loading secrets from '/_conf/ipsec/connections/XGtoO
PNsense.secrets'
2021-01-11 20:22:22 22[CFG] loaded IKE secret for 124.1XX.4X.1XX %any
2021-01-11 20:22:22 22[CFG] loaded IKE secret for 17X.2X.1X.2XX 1YY.2Y.Y.2YY
2021-01-11 20:22:22 21[CFG] rereading ca certificates from '/_conf/ipsec/ipsec.d
/cacerts'
2021-01-11 20:22:22 24[CFG] vici initiate 'XGtoOPNsense-1'
2021-01-11 20:22:22 16[IKE] <XGtoOPNsense-1|1> unable to resolve %any, retrying
in 60s
2021-01-11 20:22:22 16[IKE] <XGtoOPNsense-1|1> ### queue_child invoking quick_mo
de_create
Any advice is highly appreciated.
Thank you,
Ed
This thread was automatically locked due to age.