XG has an SG as upstream firewall. No blocked traffic during pattern updates. Worked nice and smooth when on MR1.
u2d.log shows nothing that concerns me (except the error 500 as described here)
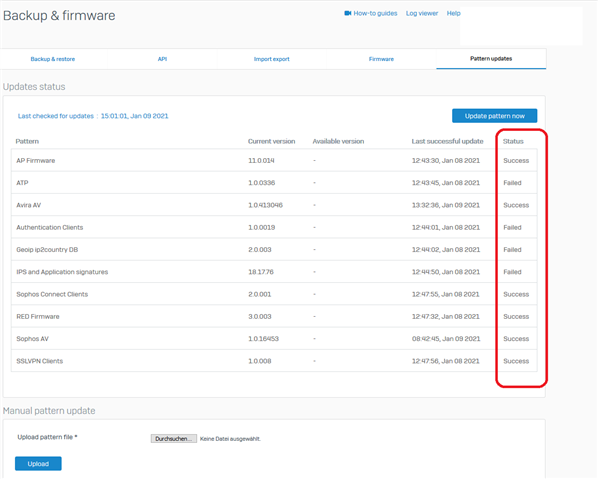
Patterns for the modules ATP, Auth Client, GeoIP, IPS and App Signatures are failing, others work.
DEBUG Jan 09 14:58:58 [16237]: Response length : 11
DEBUG Jan 09 15:01:01 [18822]: --serial = C4207AXxxxxxxxxx
DEBUG Jan 09 15:01:01 [18822]: --deviceid = xxxxxxxxxxxxxxxxxxxxxx
DEBUG Jan 09 15:01:01 [18822]: --fwversion = 18.0.4.506
DEBUG Jan 09 15:01:01 [18822]: --productcode = CN
DEBUG Jan 09 15:01:01 [18822]: --model = XG430
DEBUG Jan 09 15:01:01 [18822]: --vendor = WP02
DEBUG Jan 09 15:01:01 [18822]: --pkg_ips_version = 18.17.76
DEBUG Jan 09 15:01:01 [18822]: --pkg_ips_cv = 16.0
DEBUG Jan 09 15:01:01 [18822]: --pkg_atp_version = 1.0.0336
DEBUG Jan 09 15:01:01 [18822]: --pkg_atp_cv = 1.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_savi_version = 1.0.16453
DEBUG Jan 09 15:01:01 [18822]: --pkg_savi_cv = 1.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_avira_version = 1.0.413046
DEBUG Jan 09 15:01:01 [18822]: --pkg_avira_cv = 4.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_apfw_version = 11.0.014
DEBUG Jan 09 15:01:01 [18822]: --pkg_apfw_cv = 1.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_sslvpn_version = 1.0.008
DEBUG Jan 09 15:01:01 [18822]: --pkg_sslvpn_cv = 1.01
DEBUG Jan 09 15:01:01 [18822]: --pkg_ipsec_version = 2.0.001
DEBUG Jan 09 15:01:01 [18822]: --pkg_ipsec_cv = 1.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_geoip_version = 2.0.003
DEBUG Jan 09 15:01:01 [18822]: --pkg_geoip_cv = 1.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_clientauth_version = 1.0.0019
DEBUG Jan 09 15:01:01 [18822]: --pkg_clientauth_cv = 2.00
DEBUG Jan 09 15:01:01 [18822]: --pkg_redfw_version = 3.0.003
DEBUG Jan 09 15:01:01 [18822]: --pkg_redfw_cv = 2.00
DEBUG Jan 09 15:01:01 [18822]: --oem = Sophos
DEBUG Jan 09 15:01:01 [18822]: --server = u2d.sophos.com
DEBUG Jan 09 15:01:01 [18822]: --port = 443
DEBUG Jan 09 15:01:01 [18822]: Added new server : Host - u2d.sophos.com, Port - 443
DEBUG Jan 09 15:01:01 [18822]: Final query string is :
?&serialkey=C4207AXxxxxxxxxx&deviceid=xxxxxxxxxxxxxxxxxxxxx&fwversion=18.0.4.506&productcode=CN&appmodel=XG430&appvendor=WP02&useragent=SF&oem=Sophos&pkg_ips_version=18.17.76&pkg_ips_cv=16.0&pkg_atp_version=1.0.0336&pkg_atp_cv=1.00&pkg_savi_version=1.0.16453&pkg_savi_patch=2&pkg_savi_cv=1.00&pkg_avira_version=1.0.413046&pkg_avira_patch=2&pkg_avira_cv=4.00&pkg_geoip_version=2.0.003&pkg_geoip_cv=1.00&pkg_clientauth_version=1.0.0019&pkg_clientauth_cv=2.00&pkg_apfw_version=11.0.014&pkg_apfw_cv=1.00&pkg_redfw_version=3.0.003&pkg_redfw_cv=2.00&pkg_sslvpn_version=1.0.008&pkg_sslvpn_cv=1.01&pkg_ipsec_version=2.0.001&pkg_ipsec_cv=1.00
DEBUG Jan 09 15:01:01 [18822]: Response code : 200
DEBUG Jan 09 15:01:01 [18822]: Response body :
<Up2Date/>
DEBUG Jan 09 15:01:01 [18822]: Response length : 11
DEBUG Jan 09 15:01:04 [18900]: --serial = C4207AXxxxxxxxxx
DEBUG Jan 09 15:01:04 [18900]: --deviceid = xxxxxxxxxxxxxxxxxxxxxx
DEBUG Jan 09 15:01:04 [18900]: --fwversion = 18.0.4.506
DEBUG Jan 09 15:01:04 [18900]: --productcode = CN
DEBUG Jan 09 15:01:04 [18900]: --model = XG430
DEBUG Jan 09 15:01:04 [18900]: --vendor = WP02
DEBUG Jan 09 15:01:04 [18900]: --pkg_sysupdate_version = 0
DEBUG Jan 09 15:01:04 [18900]: Added new server : Host - eu-west-1.u2d.sophos.com., Port - 443
DEBUG Jan 09 15:01:04 [18900]: Added new server : Host - ap-northeast-1.u2d.sophos.com., Port - 443
DEBUG Jan 09 15:01:04 [18900]: Added new server : Host - us-west-2.u2d.sophos.com., Port - 443
DEBUG Jan 09 15:01:04 [18900]: Final query string is :
?&serialkey=C4207AXxxxxxxxxx&deviceid=xxxxxxxxxxxxxxxxxxxxx&fwversion=18.0.4.506&productcode=CN&appmodel=XG430&appvendor=WP02&useragent=SF&oem=&pkg_sysupdate_version=0
DEBUG Jan 09 15:01:05 [18900]: Response code : 500
DEBUG Jan 09 15:01:05 [18900]: Response body :
<?xml version="1.0" encoding="iso-8859-1"?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en" lang="en">
<head>
<title>500 - Internal Server Error</title>
</head>
<body>
<h1>500 - Internal Server Error</h1>
</body>
</html>
DEBUG Jan 09 15:01:05 [18900]: Response length : 369
ERROR Jan 09 15:01:05 [18900]: Received invalid top level tag html, expecting Up2Date
ERROR Jan 09 15:01:05 [18900]: FATAL : Error in parsing response, exiting.
DEBUG Jan 09 15:04:39 [23158]: --serial = C4207AXxxxxxxxxx
DEBUG Jan 09 15:04:39 [23158]: --deviceid = xxxxxxxxxxxxxxxxxxxxxx
DEBUG Jan 09 15:04:39 [23158]: --fwversion = 18.0.4.506
DEBUG Jan 09 15:04:39 [23158]: --productcode = CN
DEBUG Jan 09 15:04:39 [23158]: --model = XG430
DEBUG Jan 09 15:04:39 [23158]: --vendor = WP02
DEBUG Jan 09 15:04:39 [23158]: --pkg_sysupdate_version = 0
DEBUG Jan 09 15:04:39 [23158]: --oem = Sophos
DEBUG Jan 09 15:04:39 [23158]: --server = u2d.sophos.com
DEBUG Jan 09 15:04:39 [23158]: --port = 443
DEBUG Jan 09 15:04:39 [23158]: Added new server : Host - u2d.sophos.com, Port - 443
DEBUG Jan 09 15:04:39 [23158]: Final query string is :
?&serialkey=C4207AXxxxxxxxxx&deviceid=xxxxxxxxxxxxxxxxxxxxx&fwversion=18.0.4.506&productcode=CN&appmodel=XG430&appvendor=WP02&useragent=SF&oem=Sophos&pkg_sysupdate_version=0
DEBUG Jan 09 15:04:42 [23158]: Response code : 200
DEBUG Jan 09 15:04:42 [23158]: Response body :
<Up2Date/>
DEBUG Jan 09 15:04:42 [23158]: Response length : 11
DEBUG Jan 09 15:12:01 [30842]: --serial = C4207AXxxxxxxxxx
DEBUG Jan 09 15:12:01 [30842]: --deviceid = xxxxxxxxxxxxxxxxxxxxxx
DEBUG Jan 09 15:12:01 [30842]: --fwversion = 18.0.4.506
DEBUG Jan 09 15:12:01 [30842]: --productcode = CN
DEBUG Jan 09 15:12:01 [30842]: --model = XG430
DEBUG Jan 09 15:12:01 [30842]: --vendor = WP02
DEBUG Jan 09 15:12:01 [30842]: --pkg_ips_version = 18.17.76
DEBUG Jan 09 15:12:01 [30842]: --pkg_ips_cv = 16.0
DEBUG Jan 09 15:12:01 [30842]: --pkg_atp_version = 1.0.0336
DEBUG Jan 09 15:12:01 [30842]: --pkg_atp_cv = 1.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_savi_version = 1.0.16453
DEBUG Jan 09 15:12:01 [30842]: --pkg_savi_cv = 1.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_avira_version = 1.0.413046
DEBUG Jan 09 15:12:01 [30842]: --pkg_avira_cv = 4.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_apfw_version = 11.0.014
DEBUG Jan 09 15:12:01 [30842]: --pkg_apfw_cv = 1.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_sslvpn_version = 1.0.008
DEBUG Jan 09 15:12:01 [30842]: --pkg_sslvpn_cv = 1.01
DEBUG Jan 09 15:12:01 [30842]: --pkg_ipsec_version = 2.0.001
DEBUG Jan 09 15:12:01 [30842]: --pkg_ipsec_cv = 1.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_geoip_version = 2.0.003
DEBUG Jan 09 15:12:01 [30842]: --pkg_geoip_cv = 1.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_clientauth_version = 1.0.0019
DEBUG Jan 09 15:12:01 [30842]: --pkg_clientauth_cv = 2.00
DEBUG Jan 09 15:12:01 [30842]: --pkg_redfw_version = 3.0.003
DEBUG Jan 09 15:12:01 [30842]: --pkg_redfw_cv = 2.00
DEBUG Jan 09 15:12:01 [30842]: --oem = Sophos
DEBUG Jan 09 15:12:01 [30842]: --server = u2d.sophos.com
DEBUG Jan 09 15:12:01 [30842]: --port = 443
DEBUG Jan 09 15:12:01 [30842]: Added new server : Host - u2d.sophos.com, Port - 443
DEBUG Jan 09 15:12:01 [30842]: Final query string is :
?&serialkey=C4207AXxxxxxxxxx&deviceid=xxxxxxxxxxxxxxxxxxxxx&fwversion=18.0.4.506&productcode=CN&appmodel=XG430&appvendor=WP02&useragent=SF&oem=Sophos&pkg_ips_version=18.17.76&pkg_ips_cv=16.0&pkg_atp_version=1.0.0336&pkg_atp_cv=1.00&pkg_savi_version=1.0.16453&pkg_savi_patch=2&pkg_savi_cv=1.00&pkg_avira_version=1.0.413046&pkg_avira_patch=2&pkg_avira_cv=4.00&pkg_geoip_version=2.0.003&pkg_geoip_cv=1.00&pkg_clientauth_version=1.0.0019&pkg_clientauth_cv=2.00&pkg_apfw_version=11.0.014&pkg_apfw_cv=1.00&pkg_redfw_version=3.0.003&pkg_redfw_cv=2.00&pkg_sslvpn_version=1.0.008&pkg_sslvpn_cv=1.01&pkg_ipsec_version=2.0.001&pkg_ipsec_cv=1.00
DEBUG Jan 09 15:12:01 [30842]: Response code : 200
DEBUG Jan 09 15:12:01 [30842]: Response body :
<Up2Date/>
DEBUG Jan 09 15:12:01 [30842]: Response length : 11
DEBUG Jan 09 15:16:01 [2468]: --serial = C4207AXxxxxxxxxx
DEBUG Jan 09 15:16:01 [2468]: --deviceid = xxxxxxxxxxxxxxxxxxxxxx
DEBUG Jan 09 15:16:01 [2468]: --fwversion = 18.0.4.506
DEBUG Jan 09 15:16:01 [2468]: --productcode = CN
DEBUG Jan 09 15:16:01 [2468]: --model = XG430
DEBUG Jan 09 15:16:01 [2468]: --vendor = WP02
DEBUG Jan 09 15:16:01 [2468]: --pkg_ips_version = 18.17.76
DEBUG Jan 09 15:16:01 [2468]: --pkg_ips_cv = 16.0
DEBUG Jan 09 15:16:01 [2468]: --pkg_atp_version = 1.0.0336
DEBUG Jan 09 15:16:01 [2468]: --pkg_atp_cv = 1.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_savi_version = 1.0.16453
DEBUG Jan 09 15:16:01 [2468]: --pkg_savi_cv = 1.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_avira_version = 1.0.413046
DEBUG Jan 09 15:16:01 [2468]: --pkg_avira_cv = 4.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_apfw_version = 11.0.014
DEBUG Jan 09 15:16:01 [2468]: --pkg_apfw_cv = 1.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_sslvpn_version = 1.0.008
DEBUG Jan 09 15:16:01 [2468]: --pkg_sslvpn_cv = 1.01
DEBUG Jan 09 15:16:01 [2468]: --pkg_ipsec_version = 2.0.001
DEBUG Jan 09 15:16:01 [2468]: --pkg_ipsec_cv = 1.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_geoip_version = 2.0.003
DEBUG Jan 09 15:16:01 [2468]: --pkg_geoip_cv = 1.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_clientauth_version = 1.0.0019
DEBUG Jan 09 15:16:01 [2468]: --pkg_clientauth_cv = 2.00
DEBUG Jan 09 15:16:01 [2468]: --pkg_redfw_version = 3.0.003
DEBUG Jan 09 15:16:01 [2468]: --pkg_redfw_cv = 2.00
DEBUG Jan 09 15:16:01 [2468]: --oem = Sophos
DEBUG Jan 09 15:16:01 [2468]: --server = u2d.sophos.com
DEBUG Jan 09 15:16:01 [2468]: --port = 443
DEBUG Jan 09 15:16:01 [2468]: Added new server : Host - u2d.sophos.com, Port - 443
DEBUG Jan 09 15:16:01 [2468]: Final query string is :
?&serialkey=C4207AXxxxxxxxxx&deviceid=xxxxxxxxxxxxxxxxxxxxx&fwversion=18.0.4.506&productcode=CN&appmodel=XG430&appvendor=WP02&useragent=SF&oem=Sophos&pkg_ips_version=18.17.76&pkg_ips_cv=16.0&pkg_atp_version=1.0.0336&pkg_atp_cv=1.00&pkg_savi_version=1.0.16453&pkg_savi_patch=2&pkg_savi_cv=1.00&pkg_avira_version=1.0.413046&pkg_avira_patch=2&pkg_avira_cv=4.00&pkg_geoip_version=2.0.003&pkg_geoip_cv=1.00&pkg_clientauth_version=1.0.0019&pkg_clientauth_cv=2.00&pkg_apfw_version=11.0.014&pkg_apfw_cv=1.00&pkg_redfw_version=3.0.003&pkg_redfw_cv=2.00&pkg_sslvpn_version=1.0.008&pkg_sslvpn_cv=1.01&pkg_ipsec_version=2.0.001&pkg_ipsec_cv=1.00
DEBUG Jan 09 15:16:02 [2468]: Response code : 200
DEBUG Jan 09 15:16:02 [2468]: Response body :
<Up2Date/>
DEBUG Jan 09 15:16:02 [2468]: Response length : 11
any idea?
This thread was automatically locked due to age.
