Hello,
we have set this up for a remote location:
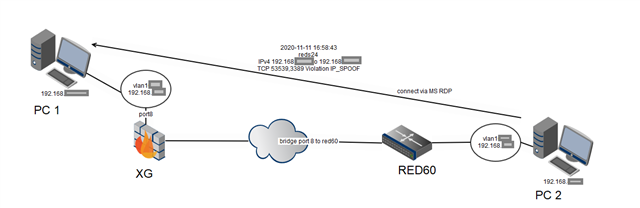
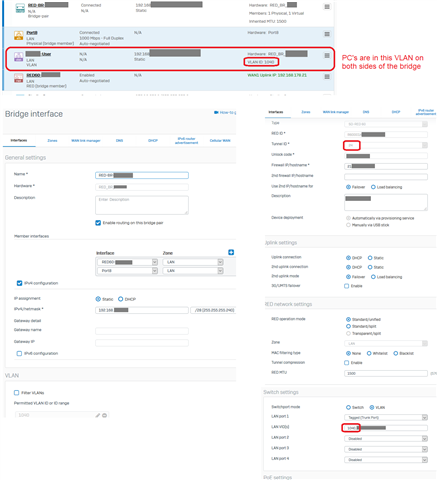
So the same VLAN ID on both sides: behind XG and behind RED, same IP Subnet.
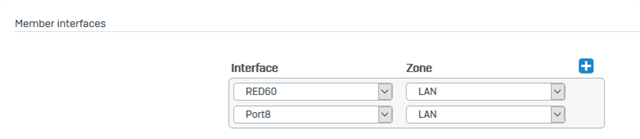
Bridge Members, same Zone:
This is already in production and working. the RED60 Users can work on internal ressources and connect to WAN via our central XG.
Now we wanted them to connect from PC2 to PC1 behind XG in the same VLAN. Thougt - no problem - no firewall rules because same subnet - easy task.
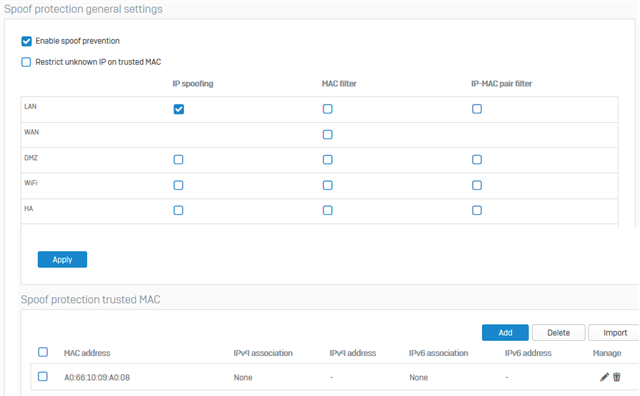
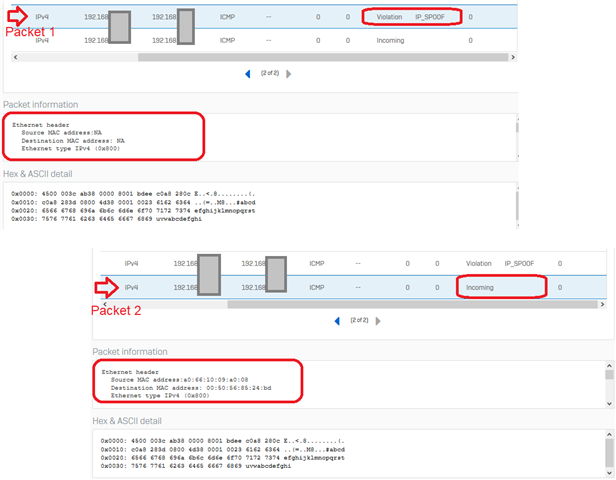
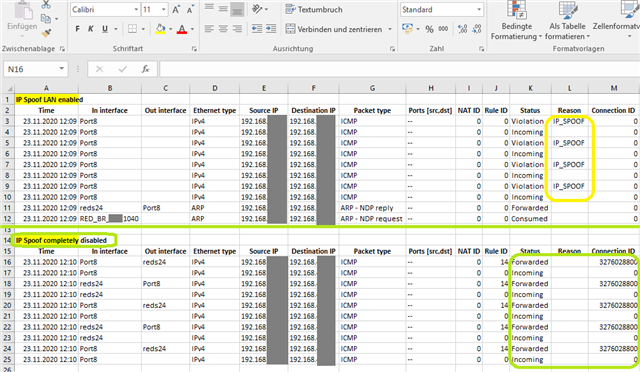
But the firewall is blocking traffic because of invalid traffic, IP SPOOF - seen in GUI packet capture. No logs in IPS by the way...!
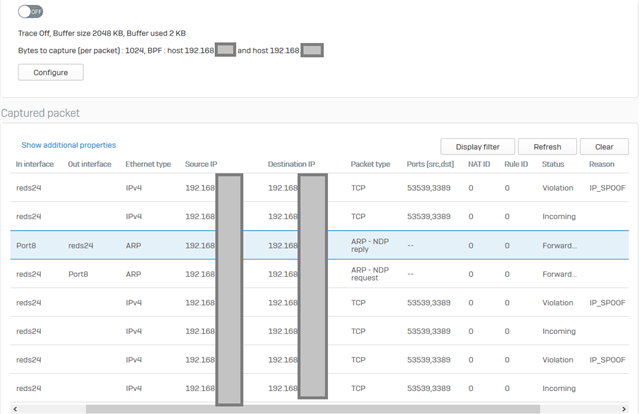
Why is this not working?
How can we get this working?
This thread was automatically locked due to age.